In my earlier article I described how preliminary Zero Belief community entry (ZTNA 1.0) options have been designed to guard organizations by limiting their publicity and lowering their assault floor. They basically work as an entry dealer to facilitate connectivity to an software. When a person requests entry to an software, the entry dealer authenticates the person and determines whether or not the person ought to have permission to entry the requested software or service. As soon as the permission is verified, the entry dealer grants entry, and the connection between the person and his or her app is established.
And that’s it. The agent not is within the image, and the person is now given full entry to no matter is inside that software with none extra monitoring from the safety system. This dynamic is called the “permit and ignore” mannequin.
ZTNA 1.0 Follows an “Enable and Ignore” Mannequin
“Enable and Ignore” could be very dangerous. Why is that, you ask? As soon as the entry dealer establishes the connection between the person and the appliance they’re attempting to entry, there isn’t a extra interrogation of the person, gadget, or software. Primarily, the dealer presumes that connection is trusted implicitly, or at the least all through that session, and all person and gadget habits for that session goes unchecked.
Verifying belief solely as soon as, with out checking once more, is a recipe for catastrophe. Extra so, it goes towards the rules of Zero Belief. In a Zero Belief mannequin, belief isn’t implicitly assumed, however somewhat one thing that needs to be constantly assessed. In any case, rather a lot can occur after belief is verified. Person, gadget, and software habits can change; functions will be compromised, and knowledge will be stolen.
Safety breaches can’t occur except somebody or one thing is allowed in to wreak havoc and trigger hurt. Actually, many trendy cybersecurity threats solely piggyback on allowed exercise to keep away from triggering alarms.
ZTNA 2.0 Leverages Steady Belief Verification
With ZTNA 2.0, steady belief verification capabilities continuously monitor for doubtlessly malicious or dangerous modifications to gadget posture, person habits, and software habits. This allows the system to reply appropriately in real-time.
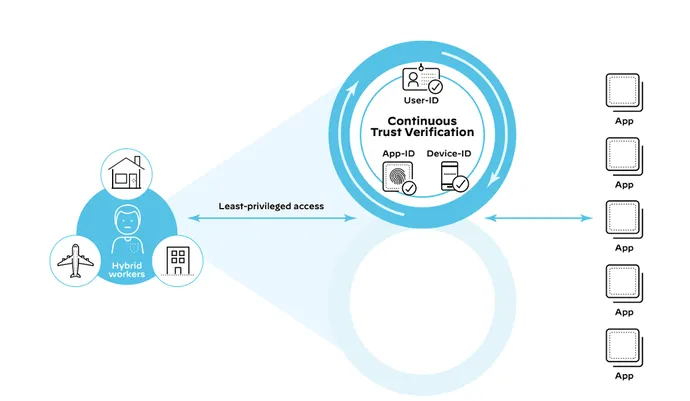
For instance, has XDR been disabled on the person’s gadget? Is a person now accessing an app from an surprising location? Is the site visitors working on port 445 really SMB? If any suspicious habits is detected, entry will be revoked in real-time.
In contrast to conventional ZTNA 1.0 approaches that leverage an app dealer, ZTNA 2.0 options needs to be deployed in-line with the site visitors, to have the ability to reply and take applicable motion towards modifications in habits, offering the perfect safety for company knowledge whereas guaranteeing optimum safety outcomes for right now’s digital workforces.
ZTNA 2.0 Is Zero Belief with Zero Exceptions
The core goal of Zero Belief is to take away implicit belief wherever potential. That’s why steady monitoring for doubtlessly dangerous modifications to gadget, software and person habits is a foundational functionality required for ZTNA 2.0. You’ll want to watch our ZTNA 2.0 digital occasion, the place we focus on extra improvements and finest practices for securing the hybrid workforce with ZTNA 2.0.

Kumar Ramachandran serves as Senior Vice President of Merchandise for Safe Entry Service Edge (SASE) merchandise at Palo Alto Networks. Kumar co-founded CloudGenix in March 2013 and was its CEO, establishing the SD-WAN class. Previous to founding CloudGenix, Kumar held management roles in Product Administration and Advertising for the multi-billion greenback department routing and WAN optimization companies at Cisco. Previous to Cisco, he managed functions and infrastructure for firms comparable to Citibank and Providian Monetary. Kumar holds an MBA from UC Berkeley Haas College of Enterprise and a Grasp’s in Laptop Science from the College of Bombay.


