SMSFactory isn’t the one malware that conducts this type of fraud. SMSFactory has thus far been present in malicious apps that should be side-loaded onto Android telephones. Nevertheless, dangerous actors have managed to sneak malicious apps bearing the Joker malware household into the Google Play Retailer time and time once more since its first look in 2017. Amongst different malicious actions, Joker subscribes its victims to paid companies through SMS.
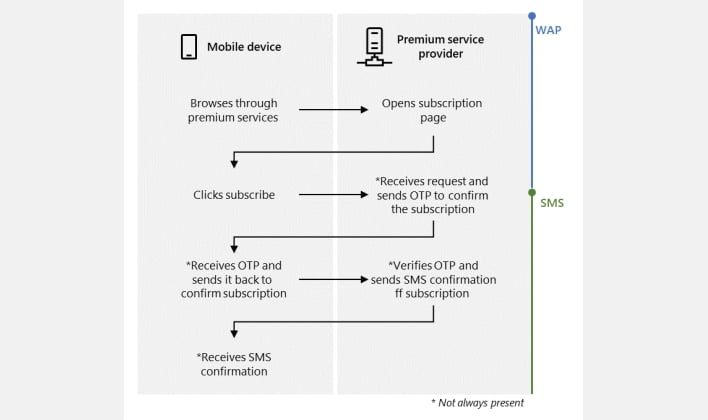
In keeping with Microsoft, the malware assault chain normally begins with the malware both disabling the Wi-Fi connection or ready for the person to modify from Wi-Fi to cell information. As soon as the contaminated cellphone is linked to a cell community, the malware navigates to a premium service subscription web page, and injects javascript into the web page that clicks the subscription button. If the WAP OTP safeguard applies, then the malware intercepts the OTP that’s despatched over textual content, sends the OTP to the service supplier, and finishes by canceling the SMS notifications which may alert the sufferer to the unauthorized premium subscription.
This automated subscription course of is a reasonably devilish strategy to commit fraud, however Microsoft has some ideas for avoiding the malware that carries out this fraud. The corporate’s 365 Defender Analysis Crew recommends that customers persist with putting in apps from the Google Play Retailer or different trusted sources and keep away from giving apps SMS permissions, notification listener entry, or accessibility entry with out understanding why the apps want these permissions. The workforce additionally suggests utilizing a trusted anti-virus resolution and retiring telephones which can be not receiving updates.


