Cybersecurity researchers from Palo Alto Networks Unit 42 disclosed particulars of a brand new safety flaw affecting Microsoft’s Service Material that could possibly be exploited to acquire elevated permissions and seize management of all nodes in a cluster.
The problem, which has been dubbed FabricScape (CVE-2022-30137), could possibly be exploited on containers which can be configured to have runtime entry. It has been remediated as of June 14, 2022, in Service Material 9.0 Cumulative Replace 1.0.
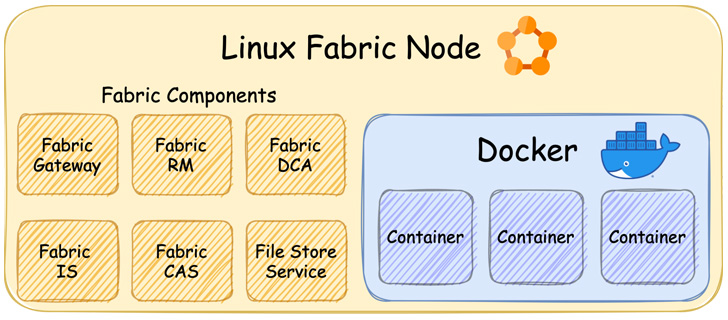
Azure Service Material is Microsoft’s platform-as-a-service (PaaS) and a container orchestrator answer used to construct and deploy microservices-based cloud purposes throughout a cluster of machines.
“The vulnerability permits a nasty actor, with entry to a compromised container, to escalate privileges and achieve management of the useful resource’s host SF node and your complete cluster,” Microsoft stated as a part of the coordinated disclosure course of.
“Although the bug exists on each Working System (OS) platforms, it is just exploitable on Linux; Home windows has been totally vetted and located to not be weak to this assault.”
A Service Material cluster is a network-connected set of a number of nodes (Home windows Server or Linux), every of that are designed to handle and execute purposes that include microservices or containers.
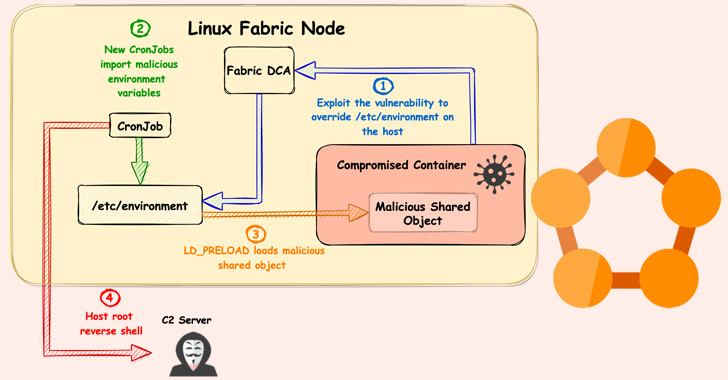
The vulnerability recognized by Unit 42 resides in a element known as Diagnostics Assortment Agent (DCA) that is liable for gathering diagnostic info and pertains to what’s known as a “symlink race.”
In a hypothetical state of affairs, an attacker with entry to a compromised containerized workload might substitute a file learn by the agent (“ProcessContainerLog.txt”) with a rogue symbolic hyperlink that might then be leveraged to overwrite any arbitrary file contemplating DCA runs as root on the node.
“Whereas this conduct could be noticed on each Linux containers and Home windows containers, it is just exploitable in Linux containers as a result of in Home windows containers unprivileged actors can not create symlinks in that surroundings,” Unit 42 researcher Aviv Sasson stated.
Code execution is subsequently achieved by making the most of the flaw to override the “/and so forth/surroundings” file on the host, adopted by exploiting an inside hourly cron job that runs as root to import malicious surroundings variables and cargo a rogue shared object on the compromised container that grants the attacker a reverse shell within the context of root.
“With a purpose to achieve code execution, we used a method known as dynamic linker hijacking. We abused the LD_PRELOAD surroundings variable,” Sasson defined. “Through the initialization of a brand new course of, the linker masses the shared object that this variable factors to, and with that, we inject shared objects to the privileged cron jobs on the node.
Though there isn’t any proof that the vulnerability has been exploited in real-world assaults up to now, it is essential that organizations take rapid motion to find out if their environments are inclined and implement the patches.