And a bug within the AWS Console when creating NACL guidelines
I had a working script however got here again later and locked down my firewall guidelines a bit tighter solely to begin getting this error. I used to be limiting visitors by way of my AWS VPC NACL based mostly on extreme abusive visitors from sure IPs and anticipated visitors for the providers I’m utilizing.
I might count on that to imagine a task and join with the above URL I might require the next visitors:
DNS (to get the IP for the area — at all times verify this primary!)
I will even want to have the ability to question Amazon DNS servers, sometimes vi the UDP protocol to port 53 from 1024–65535.
I will even want to permit the return visitors from AWS DNS Servers from port 53 again to the assigned port within the vary of 1024–65535.
Outbound for HTTP (to permit net requests to the IP tackle)
native host to sts.[region].amazonaws.com on port 443 from a port within the vary of 1024–65535.
return visitors on ports 1024–65535 or in different phrases visitors from sts.[region].amazonaws.com on these ports again to 443.
Timeout Error Connecting to an AWS Service
I believed I had that every one arrange however I’m getting this error message and presume the issue is with my NACL guidelines since that’s what I simply modified.
Join timeout on endpoint URL: “https://sts.[region].amazonaws.com/"
When working with AWS NACLs you could perceive that they’re stateless. In contrast to a safety group that can enable any return visitors for a profitable request, you could explicitly enable and deny inbound and outbound parts of the above visitors.
That’s a ache, you suppose. Nevertheless it has some safety benefits I talk about in my cloud safety lessons. However for now let’s repair this downside.
First, I can be certain that DNS is working by querying DNS for the area title I’m making an attempt to make use of and ensure I get again a sound response.
If I kind this command:
dig sts.us-west-2.amazonaws.com
I get this response:
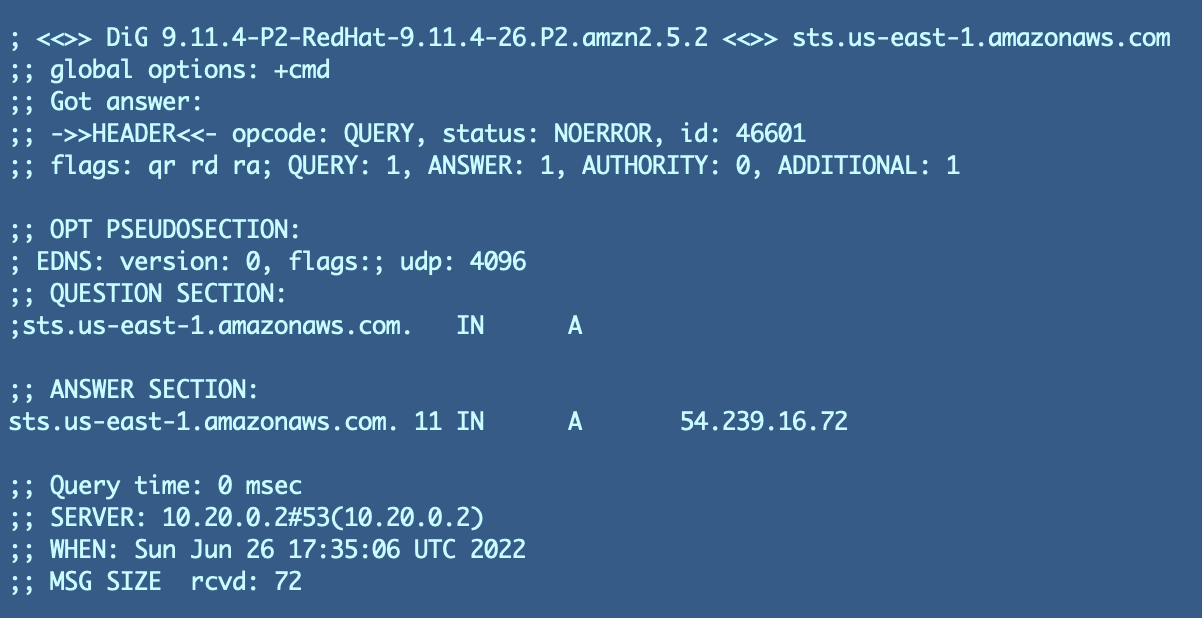
Which means I’ve the proper guidelines in place to permit making DNS queries and receiving responses since I’m getting again an IP tackle (the ANSWER SECTION reveals 54.239.16.72). If you don’t get an IP tackle reply on your DNS question:
Verify the area you’re querying:
Verify that you’re utilizing the proper area title with out https:// and with out a slash or another a part of the URL on the finish.
DNS rule on your NACL:
Permit outbound to port 53 UDP to your DNS servers.
Permit inbound 1024–65535 UDP out of your DNS servers.
Make sure that the precedence or index quantity for the rule is above the default deny rule as a result of the NACL guidelines are evaluated so as. As soon as a rule matches, it will likely be utilized to the visitors, ranging from the highest.
DNS rule on your Safety group
Permit outbound to port 53 UDP to your DNS Servers.
Be aware that it doesn’t matter what order you add this rule in your safety group since all the foundations are evaluated as a set, not an ordered checklist.
Additionally word that you simply shouldn’t have so as to add a rule for the return visitors because the safety group is stateful. That’s a mistake I made at Capital One once I first began and a community engineer pointed it out to me.
HTTPS timeout
So now the query is, why they timeout making an attempt to succeed in the service?
If I attempt to curl that area title:
curl https://sts.us-east-1.amazonaws.com
It instances out. It should hold for some time and eventually give me the timeout error message.
To confirm that isn’t an anticipated outcome, I can question from a special machine. If I run that very same command on my native laptop computer on a special community, it doesn’t timeout however returns instantly with an empty response.
Only for sanity I’ll verify the AWS standing dashboard to ensure nothing is down. If I’m going to this URL:
https://well being.aws.amazon.com/well being/standing
I see there are not any open and up to date points.
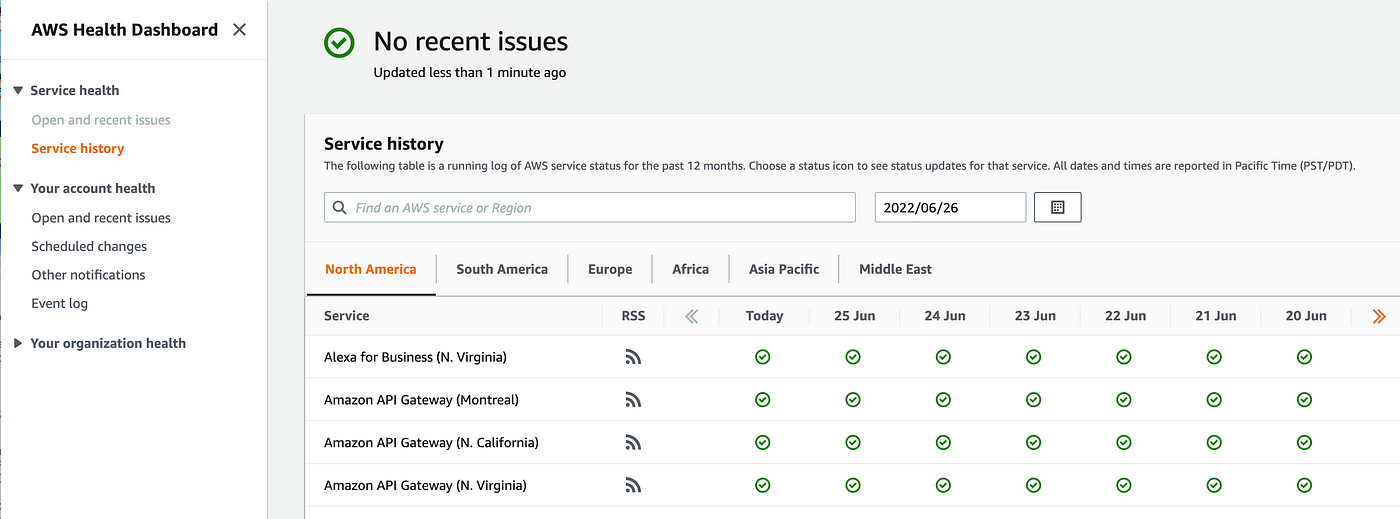
Let’s attempt to seek for the precise service that isn’t working for us:
Sadly the Safety Token Service or STS isn’t on this dashboard:

I can seek for IAM. I assume it would fall below that however I’m unsure.
No points.

I additionally wish to verify Down Detector as a result of usually issues present up there first:
https://downdetector.com/standing/aws-amazon-web-services

Experiences appear minimal and the location says there are not any points.
Let’s revisit our NACL guidelines.
- Do I enable port 443 outbound to the required AWS IP Ranges? Verify.
- Do I enable return visitors from AWS IP Ranges to excessive ports (1024–65535)
Looks like I do.
I can verify my VPC movement logs for the IP tackle I’m making an attempt to entry and question by port 443:

Seems to be like some connections are profitable from my native IP tackle to Amazon IP addresses. Hmm.

Now I’m a bit at a loss. What’s going on right here?
Safety Group Guidelines
I believed I had solely modified my NACLs however I’m going again to verify my safety group anyway as a result of that’s one of many solely different issues it could possibly be. That’s odd. I see some entries I don’t recall making and I don’t suppose I ever would as a result of they’re completely incorrect. That could be very unusual. However anyway I eliminated them and added within the following:
1 Outbound rule for HTTPS port 443 to any IP tackle.
1 Outbound rule for DNS port 53 UDP.
My inbound SSH rule from solely my very own IP tackle solely (vital!) is working. I enable no different inbound visitors to this host besides return visitors to my outbound requests.
Route Desk
Only for the sake of completeness, I do know my route desk has an Web Gateway route to permit visitors to and from the Web, in any other case SSH wouldn’t be working.
Unusual Community Habits
Properly that is all fairly unusual as a result of it looks like all the things is appropriate. I’ve been fidgeting with the foundations so let’s verify the NACL yet one more time.
Be aware that as a result of this wasn’t working, I had eliminated my extra restricted outbound guidelines and arrange two customized guidelines for ALL TCP and ALL UDP outbound. That’s a bit higher than permitting any protocol although it’s nonetheless very broad.
Right here’s what I didn’t notice. I feel once I was enhancing my customized TCP rule to permit all TCP ports my AWS SSO session timed out and one thing odd occurred to my community rule and I didn’t discover. I used to be making an attempt to create a customized TCP rule to permit all visitors however the one port that received saved was 0. I don’t even know for positive the way it received like this as a result of that is clearly not appropriate. After I noticed “ALL TCP” I simply presumed it actually was all tcp and didn’t discover the port quantity.

What I later realized is that if you happen to select a “Customized TCP” rule and solely enter port “0” it should save the rule as “ALL TCP” which isn’t appropriate. I might by no means deliberately create that rule so I believed perhaps the 0 received in there as a result of I selected “All TCP” however I re-tested and that didn’t occur. At any price, the console is totally incorrect and has a bug.
Repair: The rule ought to NOT state that it's an “All TCP” rule when the port is restricted to 0 solely. 0 doesn't and shouldn't be used to symbolize any port. It ought to be a "Customized TCP" rule. Somebody ought to be capable of create a rule for port 0 solely and that isn't an "All TCP" rule.
I found this as a result of in some unspecified time in the future, I arrange a rule particularly for outbound visitors to my IP tackle on ports 1024–65535 to repair SSH connectivity when that began failing and resolved my SSH woes. I’m not even positive precisely why SSH began failing however that rule mounted the issue.
Properly I believed I had a correct ALL TCP rule so didn’t actually need that particular rule so I deleted the extra particular SSH outbound port rule. SSH failed once more. That’s once I realized there was an issue with the “ALL TCP” rule. It wasn’t actually “ALL TCP.” There was no different rationalization.
I modified it to “Customized TCP” and explicitly added ports 0–65535 and all the things all began working. After I did that I observed it reverted to “ALL TCP” once more and didn’t present my port vary. That’s technically appropriate however not what I entered. I really feel that it is best to save what the shopper enters.
Simply to substantiate that I edited the document to customized ports I selected a special vary ending in 65534 and I observed that additionally switched the entry from “Customized TCP” to “All TCP” but it surely saved my port vary. That’s not technically appropriate as restricted ports are allowed, not “ALL TCP.”

What I didn't check and somebody ought to is whether or not, given the above rule, somebody can connect with port 65534 though it says All TCP. I presume you possibly can’t attributable to my very own problems.
So in the long run, this complete train in wasted time was attributable to a console bug that doesn’t present correct info and threw me off.
The issue with bugs like that is that you simply begin eradicating all of your restrictive guidelines to attempt to discover the issue and find yourself weakening your community safety. Now I want to return and redo all my community safety. Nice.
Oh and by the best way I used the AWS connectivity checker and it’s just about ineffective. It returned “No Path.” Yeah thanks I do know. However is the issue with a safety group or a NACL rule, ingress or egress, and/or the route desk. Inform me all the precise factors the place the visitors is blocked.
Characteristic Request: Hey AWS, it ought to be fairly straight ahead to repair the connectivity checker to pinpoint the place a change is required to repair the issue. I can do that myself with a number of queries and I do use instruments like that whereas pentesting.
At any price as soon as you possibly can attain the service on the community, the error ought to go away.
Warning: In case your group makes use of a firewall or proxy over and above the AWS Networking, you’ll want to ensure these are additionally not blocking your entry to a service endpoint. In case your visitors hits one among your company community home equipment earlier than it will get to the AWS service that community equipment is also the offender.
Teri Radichel — Comply with me @teriradichel on Twitter
© 2nd Sight Lab 2022
____________________________________________
About this weblog:
Wish to study extra about Cybersecurity and Cloud Safety? Take a look at: Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Sources by Teri Radichel: Cybersecurity and Cloud safety lessons, articles, white papers, displays, and podcasts



