Shortly after hitting
Parker Hannifin Company, a serious element provider for Boeing and Lockheed Martin, the Conti ransomware group
deserted the Conti title and break up off into smaller teams that coordinate with the bigger group’s management. This transfer got here after Conti focused the federal government of Costa Rica with
ransomware. By focusing on a authorities, the ransomware group might have invoked state actors to extend their efforts to take down Conti management, forcing the group to interrupt aside into smaller cells for elevated operations safety (OPSEC). Even earlier than the assault on Costa Rica’s authorities, the US Division of State introduced a $10 million reward for info that helps determine or find key members of the Conti ransomware group.
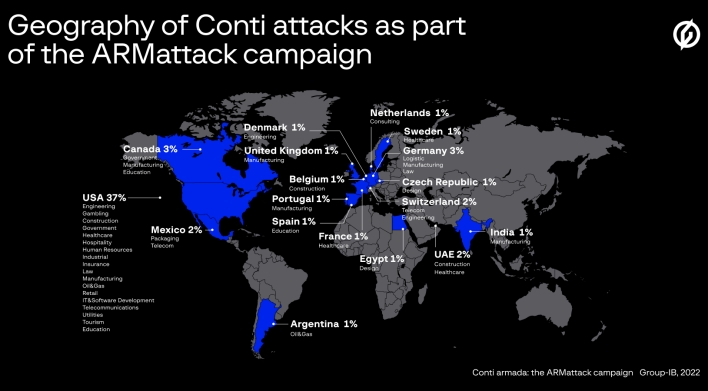
Whereas Conti might not be working below that title, cybersecurity researchers are nonetheless analyzing assaults perpetrated by the group earlier than its dissolution. Researchers on the cybersecurity agency Group-IB have printed a report detailing a selected ransomware marketing campaign carried out by Conti between November 17 and December 20, 2021. In keeping with Group-IB, the marketing campaign, codenamed “ARMattack,” was one of many ransomware teams’ quickest and best campaigns.
In somewhat below 5 weeks, the Conti ransomware gang compromised the pc methods of over 40 corporations internationally, with the plurality being situated within the US. Due to actors in several time zones, Conti was in a position to function 14 hours out of the day throughout this marketing campaign and accomplished one assault in simply three days. As soon as the group efficiently gained unauthorized entry to a community, it will exfiltrate key paperwork, together with information containing passwords, then carry out privilege escalation and acquire entry to all desired units. Lastly, the group would deploy ransomware to all compromised units, encrypting the information inside, and publicize the assault on the group’s devoted leak web site, threatening to publicly launch the encrypted knowledge if the ransom wasn’t paid.
It’s price nothing that the ARMattack marketing campaign didn’t hit a single firm situated in Russia. Conti is a Russian-speaking group and, past the unstated rule that Russian cybercriminals don’t assault Russian corporations, the ransomware group has made public statements declaring its allegiance to Russia and its authorities. When Russia started its invasion of Ukraine, the Conti ransomware gang introduced its full assist of the Russian authorities and threatened to conduct counterattacks towards anybody who carried out cyberattacks or different offensive measures towards Russia.