A brand new Golang-based peer-to-peer (P2P) botnet has been noticed actively concentrating on Linux servers within the training sector since its emergence in March 2022.
Dubbed Panchan by Akamai Safety Analysis, the malware “makes use of its built-in concurrency options to maximise spreadability and execute malware modules” and “harvests SSH keys to carry out lateral motion.”
The feature-packed botnet, which depends on a fundamental listing of default SSH passwords to hold out a dictionary assault and develop its attain, primarily capabilities as a cryptojacker designed to hijack a pc’s assets to mine cryptocurrencies.
The cybersecurity and cloud service firm famous it first noticed Panchan’s exercise on March 19, 2022, and attributed the malware to a probable Japanese risk actor based mostly on the language used within the administrative panel baked into the binary to edit the mining configuration.
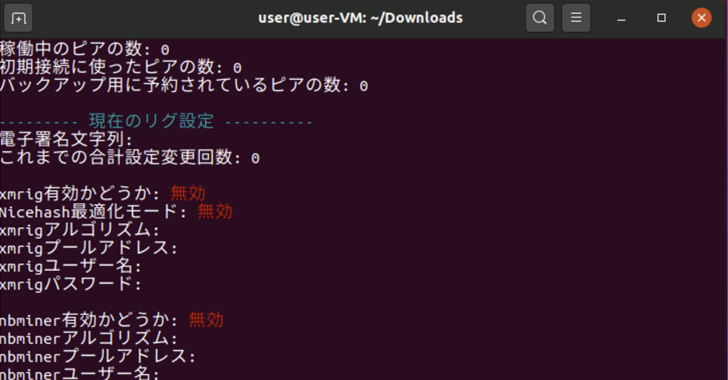
Panchan is understood to deploy and execute two miners, XMRig and nbhash, on the host throughout runtime, the novelty being that the miners aren’t extracted to the disk to keep away from leaving a forensic path.
“To keep away from detection and cut back traceability, the malware drops its cryptominers as memory-mapped recordsdata, with none disk presence,” the researchers mentioned. “It additionally kills the cryptominer processes if it detects any course of monitoring.”
Of the 209 contaminated friends detected up to now, 40 are mentioned to be presently energetic. A lot of the compromised machines are positioned in Asia (64), adopted by Europe (52), North America (45), South America (11), Africa (1), and Oceania (1).
An attention-grabbing clue as to the malware’s origins is the results of an OPSEC failure on the a part of the risk actor, revealing the hyperlink to a Discord server that is displayed within the “godmode” admin panel.
“The principle chat was empty besides a greeting of one other member that occurred in March,” the researchers mentioned. “It may very well be that different chats are solely obtainable to larger privileged members of the server.”