Whereas software-as-a-service helps organizations enhance productiveness and agility, it additionally provides complexity to the enterprise setting as IT safety groups have to have visibility over the information saved in every of the functions.
And when organizations combine SaaS functions with different SaaS functions, the assault floor grows much more as a result of extra functions have entry to the company knowledge. For instance, connecting Asana to Google Workspace offers the duty administration platform entry to knowledge saved within the productiveness suite.
In a latest report from Valence Menace Labs, 56% of CISOs mentioned they do not have a course of in place, or will not be glad with the method they’ve, for locating and managing SaaS-to-SaaS connections and integrations.
Understanding SaaS Mesh
SaaS mesh refers to connecting a SaaS utility with one other SaaS, utilizing strategies akin to OAuth and API tokens, low-code/no-code workflow, and SaaS marketplaces. Examples embrace utilizing third-party platforms akin to Heroku to entry GitHub repositories through OAuth consumer tokens, or creating and sending electronic mail campaigns from the group’s web site utilizing the API as an alternative of logging into Mailchimp’s platform. It’s attainable to finish a activity in Asana and have a corresponding notification message be printed in Slack.
Connecting SaaS instruments to core enterprise functions akin to Workplace 365, Salesforce, and Google Workspace inside a SaaS mesh helps improve the group’s agility, productiveness, and collaboration. Nevertheless, if the mesh is not managed appropriately, it may possibly expose knowledge saved in business-critical functions, in accordance with Valence Menace Labs.
The common group makes use of round 80 SaaS functions — BetterCloud estimates that organizations with greater than 1,000 staff use greater than 150 functions, whereas organizations with 50 staff or much less use solely 16 SaaS functions. When requested what number of SaaS-to-SaaS connections and third-party integrations are linked to core SaaS functions (akin to Workplace 365, Salesforce, and Google Workspace), 50% of CISOs mentioned they’ve 200 or fewer integrations, or that they did not know, Valence Menace Labs discovered.
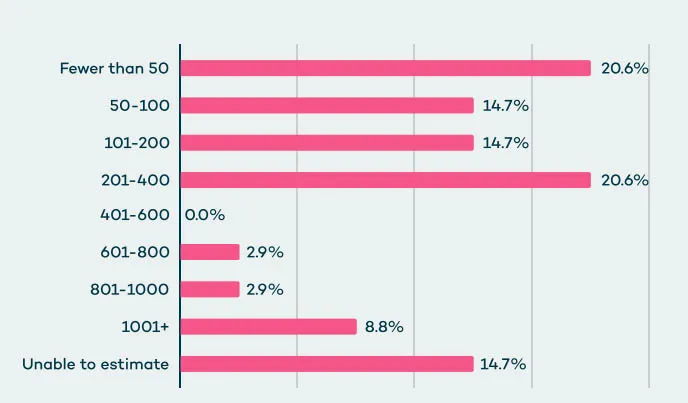
Genuinely, the common group has 917 SaaS-to-SaaS third-party integrations, in accordance with Valence Menace Labs.
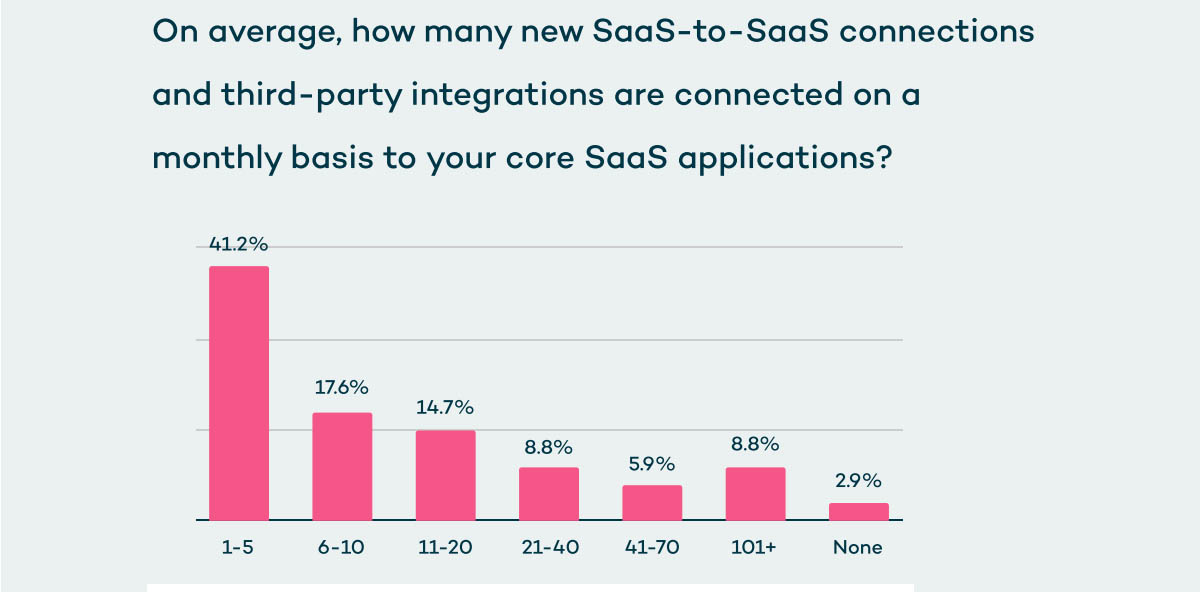
Whereas 76% of CISOs suppose below 20 new integrations are added each month to their setting, in actuality, 76 new third-party integrations are onboarded each 30 days.
Over-Provisioned Connections
When requested if that they had a course of in place to find out if an integration is overprivileged, 53% of CISOs within the Valence Menace Labs report mentioned they didn’t. This can be a drawback as a result of almost half, or 48%, of SaaS integrations (443 integrations, to be particular) are unused, and lots of of them have extra privileges than they want. A SaaS-to-SaaS integration is normally inactive as a result of somebody forgot to show it off after testing out the mixing after which deciding to not use it. However as a result of the mixing continues to be there, another person who features entry to 1 utility now has entry to the opposite and might transfer laterally.
“Most organizations shouldn’t have a steady course of in place that permits them to evaluate the enterprise justification of non-human identities and correctly offboard pointless third-party distributors,” Valence Menace Labs mentioned in its report.
Low-code/no-code platforms akin to Workato, Zapier, and Microsoft Energy Platform are highly effective as a result of non-developers can pull collectively workflows to entry knowledge from a number of sources. Nevertheless, if they don’t seem to be configured appropriately, they’ll expose knowledge erroneously. As a result of these platforms usually will not be managed by utility safety or IT safety groups, CISOs might not even know these instruments exist or are accessing enterprise functions. Within the Valence Menace Labs report, 35% of CISOs mentioned they don’t have low-code/no-code platforms of their setting, when it seems over 96% of firms have at the very least one such platform in use. In truth, the common group has 4 or 5, in accordance with the report.
Within the report, 85% of CISOs mentioned they didn’t have applicable visibility and safety from the dangers of SaaS-to-SaaS connections and third-party integrations. “The truth that 85% of CISOs had been sad with the present options suggests the necessity for extra options particularly designed to guard the SaaS mesh,” Valence Menace Labs mentioned in its report.