Because the stakes for securing on-line property proceed to rise, moral hacking permits organizations to legally get perception into the workings of menace actors and enhance their safety posture by means of safety professionals.
Moral hacking instruments simulate cyberattacks on techniques, functions, and networks to reveal vulnerabilities that hackers enjoyment of exploiting.
The ever-rising sophistication of cyberthreats makes moral hacking software program and instruments a necessity for companies that worth their cybersecurity.
Listed below are our 8 selections for the highest moral hacking software program and instruments:
Prime moral hacking software program and instruments comparability
Since there’s no scarcity of moral hacking software program, it’s essential to grasp the capabilities of the instruments in consideration to make an knowledgeable determination. Right here’s a comparability of our high picks primarily based on their options and pricing.
| Community scanning | Internet vulnerability scanning | SQLi detection | Exploit growth | Protocol evaluation | Cloud-based | Automated scanning | Beginning worth | |
|---|---|---|---|---|---|---|---|---|
| Nmap | ✔ | ✘ | ✘ | ✘ | ✔ | ✘ | ✘ | Free |
| Intruder | ✔ | ✔ | ✔ | ✘ | ✘ | ✔ | ✔ | $160/mo. for 1 utility |
| Invicti | ✘ | ✔ | ✔ | ✘ | ✘ | ✘ | ✔ | Seek the advice of Invicti |
| Metasploit | ✔ | ✔ | ✔ | ✔ | ✘ | ✘ | Partial | Seek the advice of Metasploit |
| Nessus | ✔ | ✔ | ✔ | ✘ | ✘ | ✘ | ✔ | $3,590/yr |
| SQLMap | ✘ | ✘ | ✔ | ✘ | ✘ | ✘ | ✔ | Free |
| Wireshark | ✘ | ✘ | ✘ | ✘ | ✔ | ✘ | ✘ | Free |
| Acunetix | ✘ | ✔ | ✔ | ✘ | ✘ | ✘ | ✔ | Seek the advice of Acunetix |
Soar to:

Nmap
Finest for community discovery and mapping
Nmap, quick for Community Mapper, is a well-liked open-source device for community discovery and safety auditing. Community and system directors can uncover gadgets working on a community and discover open ports together with varied attributes of the community, amongst different providers.
Nmap runs on all main pc working techniques, exhibiting its versatility, which strengthens its place as a best choice for assessing the safety posture of networks.
Pricing
Nmap is open-source and free to make use of, which means you need to use and distribute in response to the phrases of their license.
Options
Determine A

- Host discovery to determine energetic gadgets on a community.
- Port scanning (Determine A) for the detection of open ports on community gadgets.
- OS detection function determines the OS of networked gadgets.
- Model detection to determine utility and repair variations.
- Scriptable interplay utilizing the Nmap Scripting Engine (NSE).
Execs
- Spectacular community discovery and mapping capabilities.
- Helps dozens of mapping and scanning methods.
- Open supply community discovery device.
Cons
- Command-line interface is perhaps intimidating for newcomers.
- Requires common updates to take care of accuracy.

Intruder
Finest for cloud-based vulnerability scanning
Intruder is a number one cloud-based vulnerability scanner that helps customers discover cybersecurity weaknesses of their on-line techniques earlier than menace actors do. It proactively scans for brand spanking new threats and supplies distinctive menace interpretation to simplify vulnerability administration and keep away from costly information breaches.
Intruder additionally gives a steady penetration testing service, strengthening it as a fantastic selection to search out weaknesses earlier than hackers with no need in-house experience.
Pricing
Intruder gives three plans: Important, Professional, and Premium. Pricing for every of them varies primarily based on the variety of functions and infrastructure targets to be scanned, beginning at $160 per 30 days for certainly one of every. You should utilize their pricing calculator, contact Intruder for a customized quote, or strive a 14-day free trial of the Professional subscription.
Options
Determine B
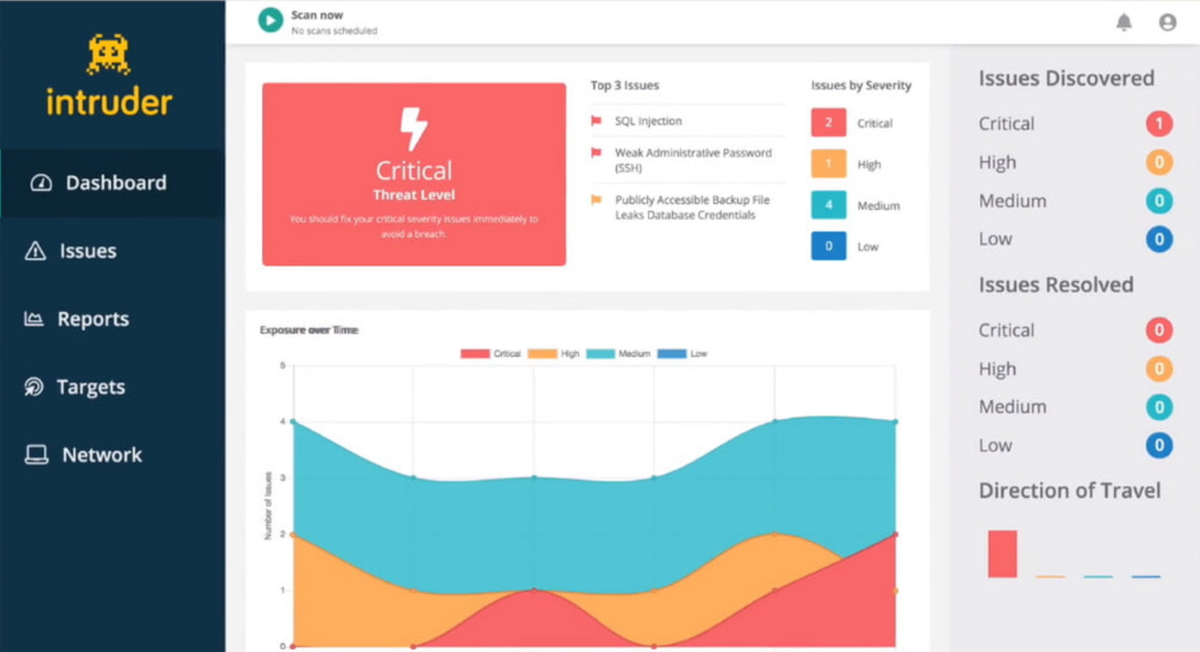
- Automated exterior, inner, cloud, internet, and API vulnerability scans (Determine B).
- Clever difficulty prioritization to visualise all vulnerabilities in a single platform.
- Steady penetration testing service.
- Easy reporting and compliance options.
Execs
- Consumer-friendly interface that’s nice for non-technical customers.
- Frequently up to date with the newest vulnerability checks.
- Delivers actionable insights and remediation recommendation.
Cons
- Pricing might be on the upper aspect for small companies.
- Restricted to on-line property and cloud environments.

Invicti
Finest for internet utility safety testing
Invicti, previously generally known as Netsparker, is an automatic utility safety testing software program that helps enterprises safe hundreds of internet sites and drastically mitigate the dangers of assaults. With a robust deal with automation, it gives a set of instruments for exposing vulnerabilities in internet functions and empowers enterprises with advanced environments to confidently automate their internet safety.
Pricing
Invicti gives two premium plans, Invicti Professional and Invicti Enterprise, although neither of them have clear pricing fashions. The corporate additionally gives a free trial and a demo, and its pricing is predicated on the variety of functions and APIs. Contact Invicti for detailed pricing.
Options
Determine C
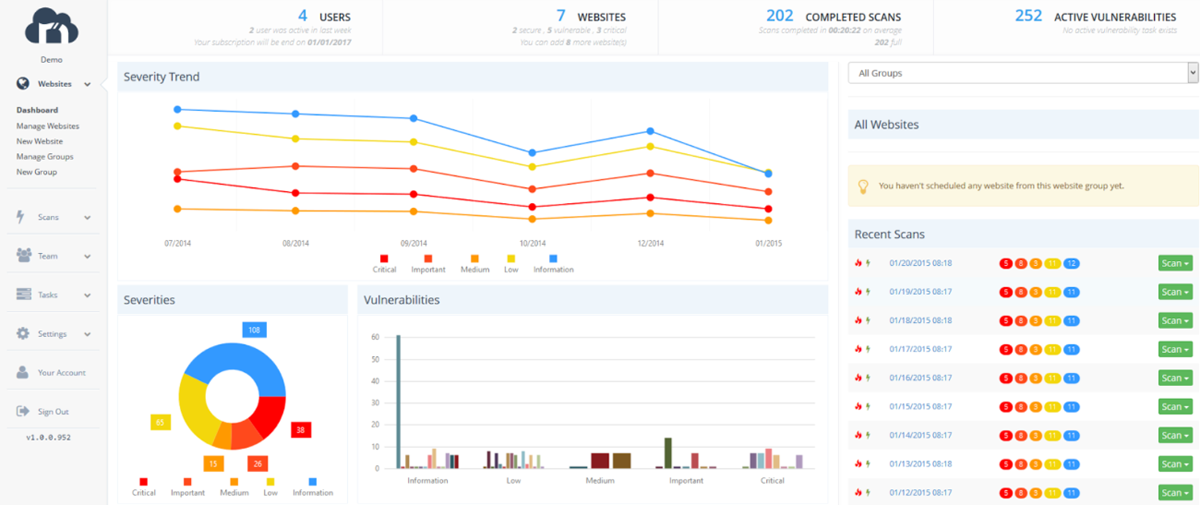
- Automated internet vulnerability scanning (Determine C).
- Superior crawling and evaluation of internet functions, web sites, and APIs.
- Detection of hundreds of vulnerabilities with nice scan accuracy.
- Detailed vulnerability reviews with remediation recommendation.
Execs
- Huge protection of internet vulnerabilities.
- Consumer-friendly interface with intuitive dashboards.
- Steady scanning and real-time alerts.
Cons
- May generate false positives that want guide verification.
- Pricing might be steep for in depth internet portfolios.

Finest for exploit growth and testing
Metasploit is a penetration testing product by Rapid7 that permits customers to soundly simulate sensible assaults on their networks to arrange their safety groups to determine, mitigate, and cease actual assaults. It has an unlimited database of payloads and exploits to extend the productiveness of penetration testers, prioritize and exhibit danger, and gauge safety consciousness utilizing real-world assault situations.
Pricing
Metasploit Framework is free and open-source, whereas Metasploit Professional gives superior options with pricing accessible upon request.
Options
Determine D
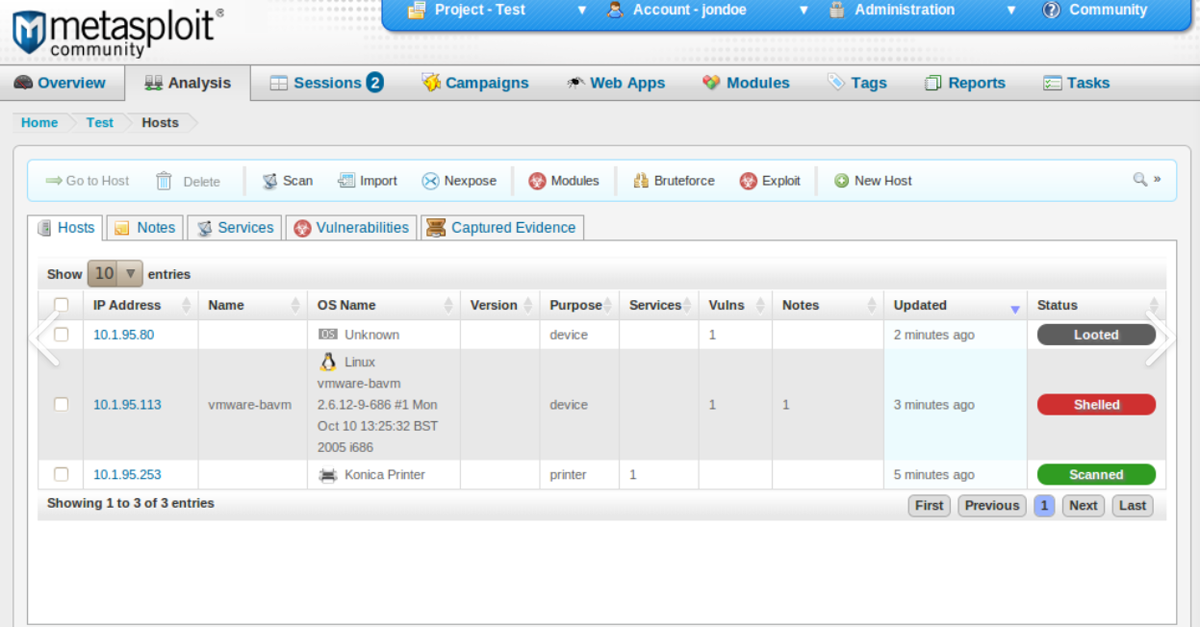
- In depth assortment of exploits and payloads.
- Potential to craft and execute customized exploits.
- Auto, guide, and post-exploitation options.
- Vulnerability validation and danger evaluation (Determine D).
Execs
- Frequently up to date with the newest exploits.
- Integration with different well-liked safety instruments.
- Nice for each newcomers and superior customers.
Cons
- The command-line interface can frustrate non-technical customers.
- It may be useful resource intensive throughout energetic scans or exploitation.

Nessus
Finest for holistic vulnerability evaluation
Nessus, some of the trusted vulnerability evaluation instruments within the cybersecurity business, gives customers a full evaluation of their surroundings in a quickly altering safety world. It’s a answer meant to simplify vulnerability evaluation and provide customers peace of thoughts in approaching vulnerabilities, leading to much less effort and time taken to evaluate and remediate points.
Pricing
Nessus gives two variations. Nessus Skilled begins at $3,590 for the primary 12 months, and Nessus Skilled begins at $5,290 — excluding help and coaching prices for every plan.
Options
Determine E
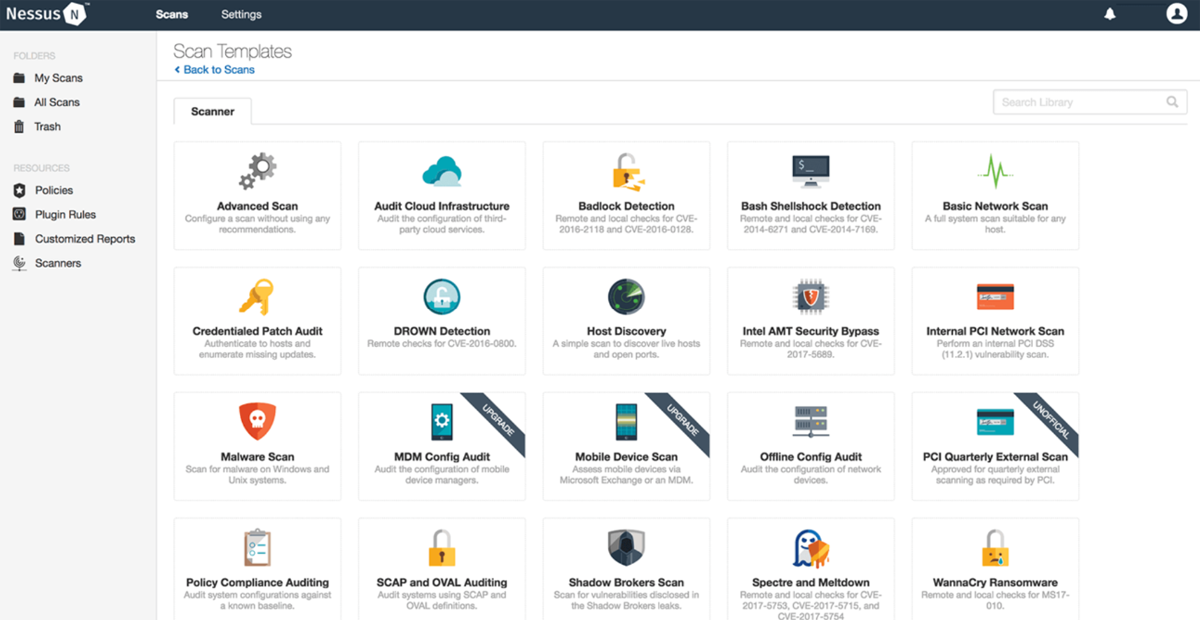
- Greater than 450 prebuilt insurance policies and templates (Determine E).
- Inner and exterior community scanning.
- Configuration audits and malware detection.
- Integration with patch administration options.
Execs
- Clear, user-friendly interface with detailed reviews.
- Frequently up to date vulnerability database.
- Helps customized plugins for tailor-made scans.
Cons
- Pricing could also be steep for smaller organizations.
- Superior configurations may require technical experience.

SQLMap
Finest for SQL injection (SQLi) detection and exploitation
SQLMap is an open-source penetration testing device that provides automated detection and exploitation of SQLi flaws and gaining management of database servers. It possesses a robust detection engine and has a dynamic set of options and switches overlaying database fingerprinting, which permits customers to acquire entry to underlying file techniques and to implement instructions on working techniques by means of out-of-band connections.
Pricing
SQLMap is free and open-source.
Options
Determine F
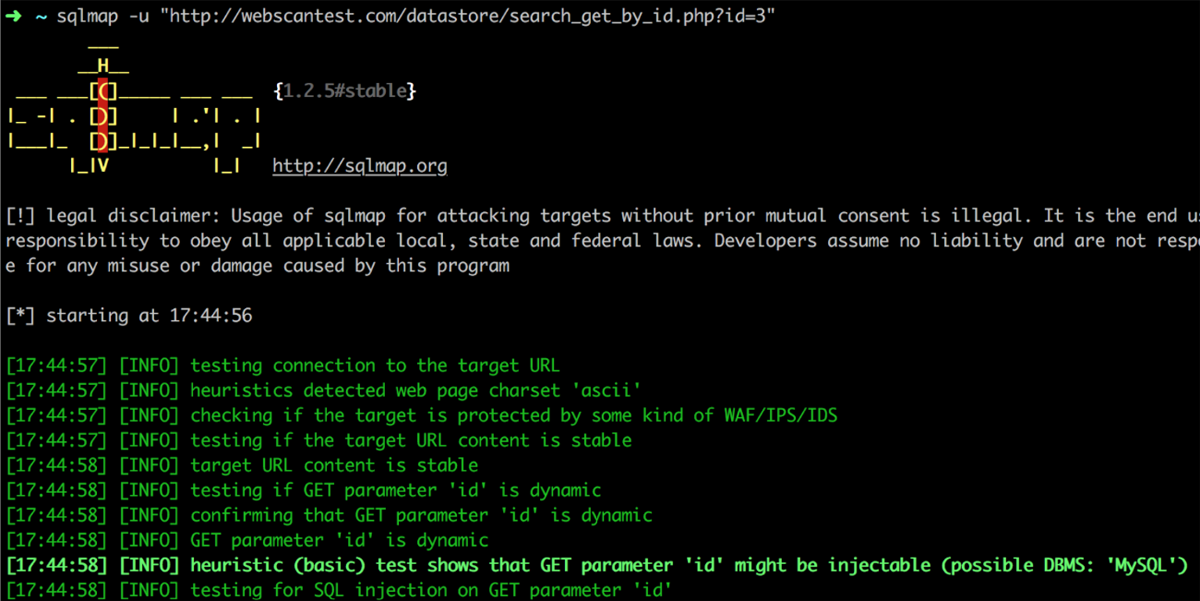
- Helps a variety of databases.
- Automated detection (Determine F) of SQLi flaws.
- Information extraction, database fingerprinting, and password hashing.
- Help for six SQLi methods.
Execs
- Thorough SQLi testing capabilities.
- SQLMap is usually up to date with new detection methods.
- It’s a command-line device with in depth documentation.
Cons
- Lack of a graphical person interface.
- Requires some data of SQL for superior exploitation.

Wireshark
Finest for community protocol evaluation
Wireshark is a famend community protocol analyzer that permits customers to seize and examine packets traversing their community. With its deep inspection capabilities, Wireshark supplies insights into community conduct, which makes it a fantastic device for community troubleshooting and safety evaluation.
Pricing
Wireshark is free and open-source.
Options
Determine G

- Deep packet inspection and evaluation (Determine G).
- Wireshark helps a variety of protocols.
- Filtering capabilities for focused evaluation.
- Graphical and command-line interfaces.
Execs
- Expansive community evaluation device.
- It’s usually up to date with help for brand spanking new protocols.
- In depth on-line documentation and neighborhood help.
Cons
- May be overwhelming for newcomers.
- It wants substantial system sources for big captures.

Acunetix
Finest for automated internet vulnerability scanning
Acunetix is an automatic safety testing device that empowers smaller safety groups to deal with giant utility safety issues, guaranteeing organizations handle danger throughout every kind of internet functions. It automates guide safety processes and immediately integrates into growth instruments to permit builders and safety groups to work seamlessly and extra effectively.
Pricing
Acunetix’s pricing will not be publicly listed. Detailed pricing is obtainable upon request.
Options
Determine H
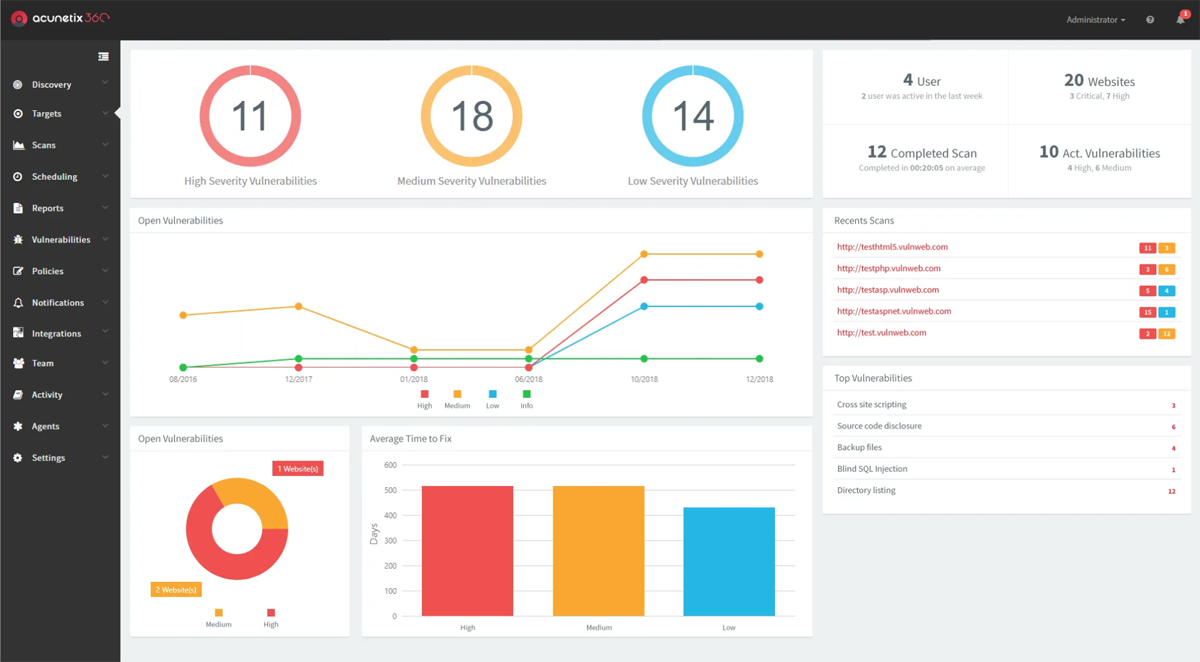
- Detection of over 7,000 internet vulnerabilities (Determine H), together with zero-days.
- DeepScan know-how for JavaScript-heavy websites.
- Built-in internet utility safety with developer instruments.
- Help for steady integration.
Execs
- Widespread internet vulnerability protection.
- Intuitive, user-friendly interface.
- Gives steady vulnerability scans.
Cons
- May be costly for organizations with in depth internet portfolios.
- It isn’t resistant to false positives.
Key options of moral hacking software program and instruments
There’s all kinds of approaches taken by moral hacking software program. Relying in your use case, you must preserve a watch out for many or all the following options.
Community scanning
With community scanning, you possibly can uncover gadgets and providers on a community and determine energetic gadgets, open ports and the providers working on them. This gives a holistic view of the community’s topology, serving to organizations perceive potential entry factors and weak spots of their infrastructure.
Internet vulnerability scanning
This function focuses on scanning internet functions to reveal vulnerabilities comparable to SQLi, cross-site scripting, and different web-specific threats. Since internet functions are key to enterprise operations right now, internet vulnerability scanning ensures their safety to forestall information breaches and preserve belief.
SQLi detection
Instruments with this function can determine potential SQLi vulnerabilities in internet functions, which regularly results in unauthorized database entry. As SQLi stays a prevalent menace, these options are fairly essential to detecting vulnerabilities and defending delicate information saved in databases.
Exploit growth and testing
Some moral hacking instruments can develop, check, and deploy customized exploits towards recognized vulnerabilities, simulating real-world assault situations. Exploit growth and testing helps to prioritize patches and countermeasures.
Protocol evaluation
Protocol evaluation is about capturing and analyzing community visitors to grasp the conduct of protocols and detect anomalies. Analyzing community visitors will show you how to detect unauthorized information transfers, ongoing cyberattacks, or different malicious actions.
Cloud-based operations
Some moral hacking instruments function within the cloud, providing scalability and distant entry capabilities. The cloud migration that defines right now’s know-how panorama echoes the necessity for instruments that may function in or assess cloud environments and guarantee constant safety posture throughout platforms.
Automated scanning
The power to scan with out guide intervention offers organizations common and constant safety assessments. Automation ensures that vulnerabilities are detected promptly, decreasing the window of alternative for attackers.
How do I select one of the best moral hacking software program and instruments for my enterprise?
To determine the moral hacking device that’s excellent for you, it is very important think about just a few components. You want to concentrate on the scope of your infrastructure. As an illustration, is your infrastructure solely web-based? Are your community and pc safety additionally in consideration? By asking these questions, you’ll achieve a greater understanding of your wants and the kind of device that satisfies them.
To slim it down even additional, you must think about the platforms supported by the instruments in consideration. Are the platforms you utilize appropriate with the instruments you’re contemplating?
The dimensions of your group and finances also needs to affect your determination. It’s good to make certain the chosen device shall be well-suited to the dimensions of your digital surroundings and whether or not you possibly can minimize prices through the use of open-source instruments for some options that handle your safety wants.
Lastly, all the time think about demos the place accessible to offer you an actual really feel of how the instruments work.
Ceaselessly Requested Questions (FAQ)
Are moral hacking instruments authorized?
Sure, moral hacking instruments are authorized when used with correct authorization and for legit functions like securing a corporation’s personal techniques. Unauthorized use towards techniques with out consent will not be solely unlawful but in addition unethical.
Can I take advantage of a number of moral hacking instruments concurrently?
Sure, many organizations use a mix of instruments to make sure they cowl their entire assault floor. Every device may provide distinctive options or be finest in particular areas, so utilizing them in tandem can present a extra holistic safety evaluation.
Is it protected to make use of moral hacking instruments?
When used appropriately and responsibly, moral hacking instruments are protected. Nonetheless, solely approved personnel ought to have entry to those instruments to forestall misuse.
Do I would like a background in cybersecurity to make use of these instruments?
Whereas some instruments are user-friendly and designed for relative newcomers, others may want a foundational understanding of cybersecurity ideas. It’s useful to have some data or coaching, particularly for extra superior instruments.
Methodology
We selected software program instruments that cowl totally different facets of moral hacking then in contrast their options, usability, and pricing. We additionally assessed their product pages and in contrast their listed choices with verified person critiques to grasp how customers reply to the listed instruments.
Backside line: Defending your group with moral hacking instruments
As hackers turn out to be extra refined, the power to legally and ethically place oneself of their sneakers with the purpose to enhance the safety posture of organizations is a necessity right now. Investing in these instruments guarantees to stage the taking part in discipline towards menace actors, serving to organizations higher safe their digital property and develop belief with their stakeholders.
There are moral hacking instruments for all sizes of groups, use instances, and budgets. Nonetheless, these instruments have to be used responsibly and with the suitable authorization to make sure that they don’t inadvertently turn out to be the threats they purpose to fight.
To make sure your workforce has the experience wanted to make use of moral hacking instruments successfully, chances are you’ll wish to have them pursue a cybersecurity certification.


