Over the previous eight months, no less than 5 Russian state-sponsored or cybercriminal teams have focused Ukrainian authorities companies and personal corporations in dozens of operations that aimed to disrupt providers or steal delicate info.
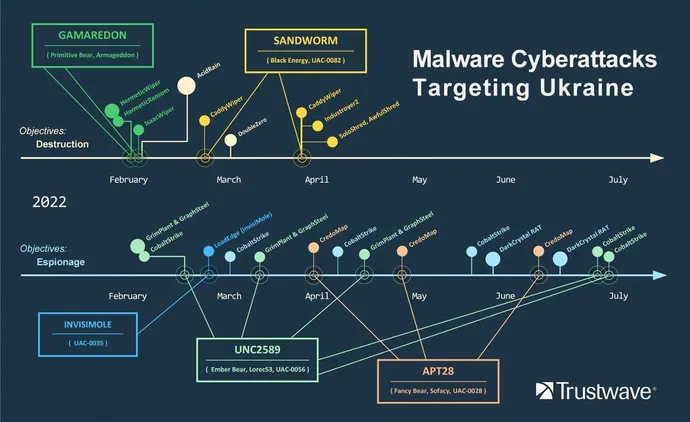
In February, state-sponsored teams equivalent to Gamaredon, Sandworm, and Fancy Bear used wiper packages in an try to break infrastructure and sabotage laptop techniques, researchers at Trustwave say in a brand new analysis be aware. These assaults lasted three months, utilizing credential stealers to realize entry to techniques.
Fancy Bear and Sandworm are beneath orders from the Primary Directorate of the Common Employees of the Armed Forces (GRU), with Gamaredon being directed by Russia’s Federal Safety Service (FSB), researchers famous.
Different cybercriminal teams with hyperlinks to Russia are additionally participating within the cyberattacks on Ukrainian targets, with common cyber-espionage operations trying to steal info and set up footholds in varied techniques for later use, Trustwave’s report states. This consists of two teams particularly, generally known as Ember Bear (aka UNC2589) and Invisimole, that are identified cybercriminal teams which will additionally collaborate with the Russian authorities, in keeping with Trustwave’s report.
Whereas citing the maxim that “we do not know what we do not know,” Karl Sigler, safety analysis supervisor at Trustwave SpiderLabs, believes that Russia is being extra apparent about its assaults.
“They aren’t making an attempt to cover their location,” he says. “They need folks to know the attribution, and for that cause, I do not suppose we’re lacking as a lot as we did this time final yr. We’re actually seeing blatant exercise.”
Cybersecurity consultants have carefully analyzed Russia’s cyber technique throughout its invasion of Ukraine to gauge the chance posed by cyberattacks and malware, used to enhance and assist the bodily invasion. Assaults preceded the precise invasion on Feb. 24, and have continued as Russia dug into japanese Ukraine and the Crimean peninsula.
“For sure, subtle cyber weapons are key instruments within the arsenal of a contemporary army,” Trustwave states within the evaluation. “With Ukraine being focused by a wide range of cyberattacks, we will clearly see that authorities belongings, important infrastructure, media, and personal sector organizations are extremely profitable targets for attackers, and even reputable penetration instruments may be hijacked and used as weapons.”
Wipers & Extra: Shifting Assault Methods
Russia’s cyber-operations technique has modified over the preliminary six months of its invasion into Ukraine.
The damaging assaults primarily occurred within the first few months of the struggle, Trustwave’s Sigler says. Each Gamaredon and Sandworm focused Ukrainian corporations and authorities companies with a wide range of wiper packages.
Gamaredon, aka Primitive Bear and Armageddon, carried out three assaults in February 2022, together with the HemeticWiper data-wiping assault, the place the group used a a stolen digital certificates from Hermetica Digital to bypass some safety measures and focused high-profile Ukrainian organizations. Sandworm (aka Black Vitality), focused Ukrainian teams with further damaging assaults, equivalent to CaddyWiper and Industroyer2.
These damaging assaults seem to have lasted only some months. Russia seemingly thought that the struggle can be rapidly received, so used the operations to hamper Ukrainian resistance, Sigler says.
“They targeted on a taking lot of issues offline, hoping that the disruption can be sufficient to tilt the scales and actually convey a few fast finish to the battle,” he says. “So I believe that, because the battle has stretched out over the months, they’re extra targeted on gathering intel to tell subsequent steps.”
Whereas the three superior persistent threats (APTs) — Gamaredon, Sandworm, and Fancy Bear — have been linked to the cyberwar assaults, Trustwave’s report notes that two others have additionally ramped up exercise. Cozy Bear is conducting operations for Russia’s International Intelligence Service (SVR), whereas DragonFly (aka Energetic Bear) is linked to the FSB.
Russia has additionally used cybercriminal teams as kind of a web based militia with a give attention to stealing info and having access to techniques, in keeping with the report. Invisimole and Ember Bear have each cooperated with the Russian authorities, finishing up out cyber-espionage operations in opposition to a wide range of targets, together with the LoadEdge assault in opposition to Ukrainian authorities companies and one other operation, dubbed GrimPlant, that infiltrated authorities companies and put in backdoors.
“Malware used within the assaults normally present backdoor entry with webcam and microphone captures, keylogging, and the likelihood to obtain and set up further parts,” the Trustwave report states. “Exfiltrated information consists of working system info, paperwork, footage and saved passwords from internet browsers and software program.”
Whereas the damaging assaults have seemingly paused, in keeping with the report, the espionage assaults are ongoing.


