In 2022, we noticed explosive transitions within the cloud safety market — each facet of the ecosystem, together with distributors, merchandise, and infrastructure, went by means of a radical change. It birthed new classes like information safety posture administration (DSPM), noticed established distributors leaping to announce cloud information lakes like Amazon Safety Lake, and put distributors by means of turmoil, like KnowBe4 being acquired by Vista Fairness for $4.3 billion.
As we sit up for 2023, cybersecurity for workloads (digital machines, containers, companies) within the public cloud will proceed to evolve, with prospects making an attempt to stability the necessity for aggressive cloud adoption and compliance with safety wants. CIOs and CISOs will problem their groups to construct the muse for a safety platform that may consolidate level merchandise, assist a number of clouds (AWS, Azure, and GCP), and leverage automation to scale safety operations. A zero-trust structure will cleared the path to workload safety within the cloud, real-time information safety, and centralized coverage enforcement. Right here’s a deeper dive into how these 5 dynamics will make their presence felt in 2023 with public cloud workloads.
Generative Assaults Will Turn out to be Focused and Customized
Automation and machine studying empower cybercriminals to launch subtle, focused assaults. Scripted botnets can conduct community reconnaissance on cloud infrastructure, and invaluable information might be harvested and used to launch additional assaults. Malware packages have gotten a commodity, with available automated instruments by which the extent of abstraction allows even unimaginative minds to turn out to be deadly. For instance, ChatGPT, which has taken the tech world by storm, can use machine studying to auto-script malware.
Cyberthreat researcher @lordx64 shared an instance of malware auto-generated by ChatGPT. The malware used PowerShell to obtain ransomware utilizing an obfuscation script, encrypt all of the recordsdata, and exfiltrate the important thing to google.com.
Centralized Safety Posture Will Turn out to be the Norm to Sort out Workload Sprawl
Misconfigurations as a consequence of human error stay the most important root reason behind cyberattacks. Many assaults use methods reminiscent of code injection and buffer overflow to prey on weak configurations. With the cloud enabling workloads to be spun up and down regularly, configuring safety insurance policies at particular person firewalls at each digital personal cloud (or a belief zone) opens the door for human error.
Organizations will more and more search for architectures that may centralize cloud safety coverage definitions, enforcements, and remediations. Solely when cyber prevention is delivered from a central platform can protection be utilized to all workloads, as a substitute of only a few choose ones.
Zero-Belief For Workload Safety Will Acquire Momentum
Zero belief will see widespread adoption to guard property by implementing an specific belief framework for all property within the public cloud. Implementing zero belief within the public cloud is completely different and distinctive as a result of prospects are coping with ephemeral and dynamic assets. With zero belief platforms that have been architectured for the cloud can carry down price overruns and complexity. Earlier than a workload in a public cloud can request a useful resource, it should undergo an intensive belief examine — one that mixes id, gadget threat, location, menace intelligence, behavioral analytics, and context. Upon efficiently establishing specific belief, the useful resource will then be topic to company safety coverage for entry management.
CIOs Will Look For Extra Efficient Multicloud Safety Instruments
On the subject of vendor greatest practices, CIOs are more and more taking a look at diversified portfolios of public cloud infrastructure for 3 primary causes. They wish to cut back reliance on a single vendor; many are additionally trying to combine infrastructure inherited from mergers and acquisitions. And CIOs have to leverage best-of-breed companies from completely different distributors, reminiscent of Google Cloud BigQuery for information analytics, AWS for cellular apps, Oracle Cloud for ERP, for instance.
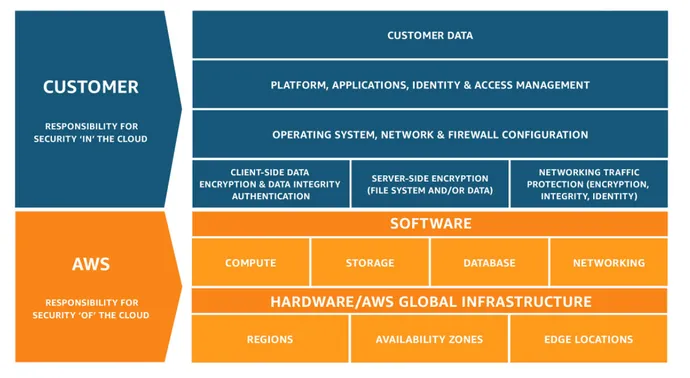
Each cloud vendor preaches the notion of “shared safety accountability,” placing the onus on the client to implement a safety infrastructure for his or her cloud assets. Savvy IT outlets guarantee they choose a cybersecurity platform that helps a number of public cloud environments.
Actual-Time Information Safety Will Be a Core Criterion for Cloud Information Governance, Safety
Securing delicate information reminiscent of protected well being data, personally figuring out data, monetary data, patents, confidential company information, and different mental property is arduous when information strikes to the cloud. Legacy information loss prevention (DLP) architectures that depend on regexes, scans, and static guidelines are inadequate and ineffective for DLP within the cloud.
The rise of the info safety posture administration class has supplied essential visibility into the necessity for observability and real-time evaluation. Proxy-based architectures that may decrypt and examine all SSL visitors will turn out to be a cornerstone for enterprises that really care about defending their delicate information.
Migration to the cloud will not be a brand new pattern within the company world, however the implications of cybersecurity for cloud workloads are nonetheless evolving. Whereas there are not any clear solutions but, these are among the main indicators prospects will use to navigate in 2023.
Learn extra Accomplice Views from Zscaler.


