It is no secret that the job of SOC groups continues to turn into more and more tough. Elevated quantity and class of assaults are plaguing under-resourced groups with false positives and analyst burnout.
Nevertheless, like many different industries, cybersecurity is now starting to lean on and profit from developments in automation to not solely keep the established order, however to achieve higher safety outcomes.
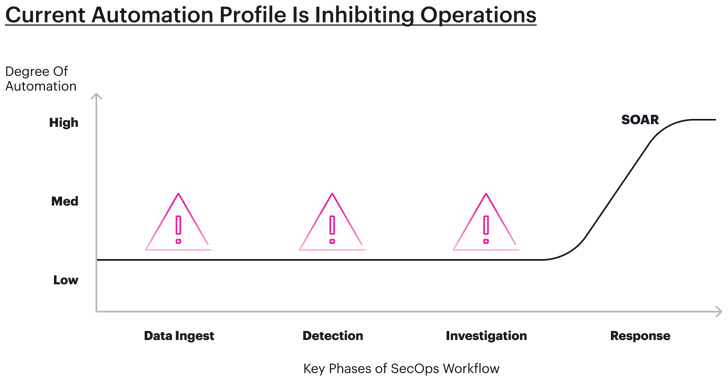
Automation throughout a number of phases of the SOC workflow
The necessity for automation is evident, and it’s obvious that it’s turning into desk stakes for the trade. Of all cyber resilient organizations, IBM estimates that 62% have deployed automation, AI and machine studying instruments and processes.
Up till now, a lot of those developments in automation have been targeted on response, with SOAR and incident response instruments taking part in an instrumental position in tackling essentially the most pressing section of the SOC workflow.
Centering the main target solely on response, nonetheless, means we’re treating the signs as an alternative of the foundation reason behind the illness. By breaking down the SOC workflow into phases, it’s straightforward to see extra situations the place automation can enhance the velocity and efficacy of safety groups.
The 4 phases the place it’s potential to develop protection of automation embody:
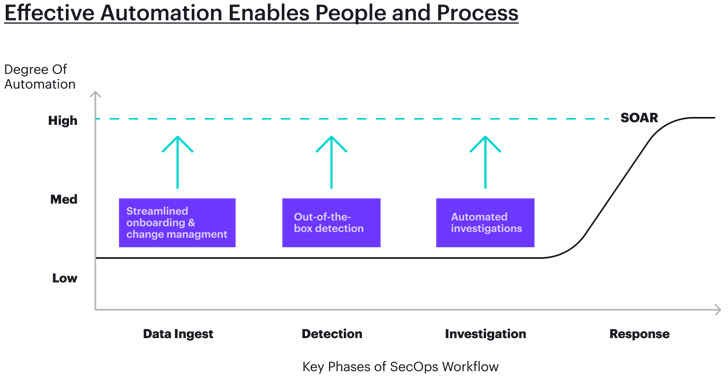
- Knowledge ingestion and normalization: Automating information ingestion and normalization can empower groups to deal with enormous quantities of knowledge from a number of sources, laying the inspiration for added automated processes
- Detection: Offloading the creation of a major proportion of the detection guidelines can liberate time for safety analysts to concentrate on the threats which might be distinctive to their group or market section
- Investigation: Offloading guide and tedious work to shorten investigation and triage processes
- Response: Mechanically responding to recognized and found threats for speedy and correct mitigation
Knowledge: Laying the inspiration for automation
Ingesting enormous quantities of knowledge might sound overwhelming to many safety groups. Traditionally, groups have had a tough time connecting information sources or have merely needed to ignore the info volumes that they could not deal with as a consequence of cost-prohibitive fashions of legacy instruments that cost for the quantity of knowledge that they retailer.
With the world frequently migrating to the cloud, it’s crucial that safety groups don’t draw back from large information. As an alternative, they should enact options that assist them handle it and in flip, obtain higher safety outcomes by having elevated visibility on your entire assault floor.
Safety information lakes have introduced with them a paradigm shift in safety operations. They help the ingestion of large volumes and number of information, on the velocity of cloud, and permit safety platforms to run analytics on prime of them with decreased complexity and at a predictable price.
Detection: Automating the 80%
As extra information is ingested, there’ll inherently be extra alerts found. Once more, this will likely sound intimidating to overworked safety groups, however automated processes, akin to out-of-the-box detection guidelines throughout assault vectors, is one other excellent instance the place automation can result in an enchancment in protection.
Typically talking, there are various similarities in the way in which networks are attacked, with roughly 80% of menace indicators being frequent throughout most organizations.
A contemporary SOC platform provides out-of-the-box detection guidelines that cowl this 80% by plugging into menace intelligence feeds, open-source data bases, social media, or darkish net boards, to create logic defending in opposition to the most typical threats. Combining these with further guidelines written by in-house safety groups, platforms are capable of maintain up-to-date with menace strategies and make the most of automated detection round them.
Investigation: Separate the sign from the noise
The investigation section of the SOC workflow is one that isn’t usually related to automation. It’s historically slowed down by quite a few instruments and guide investigations limiting the effectivity and accuracy of safety groups.
The processes that may be bolstered with automation throughout the investigation section embody:
- Menace-centric clustering of alerts: Safety instruments provides you with hundreds of alerts, however in actuality these boil all the way down to only some threats. At scale, this turns into an unlimited useful resource drain. If the alerts are mechanically grouped based mostly on their menace context, then safety analysts can extra simply perceive and reply to single incidents versus chasing a whole lot of alerts and false-positives.
- Enrichment: By mechanically enriching the entities related to every sign or alert with further data from many alternative information sources, groups get all of the out there context to know the danger of the alert.
- Correlation: Mechanically correlating occasions results in higher visibility into the trail of attackers throughout the group’s community.
- Visualization: As soon as correlated, assault “tales” will be mapped and visualized in an easy-to-read timeline making it simpler for analysts and different stakeholders to achieve clear insights.
Collectively, these automated duties supply analysts quick indications of which incidents are the best precedence and wish additional investigation. This can be a drastic enchancment in comparison with legacy methods the place analysts are continually checking and rechecking incidents, investigating redundancies and manually piecing collectively occasions.
Automated investigation, when together with guide search practices, can result in extra actual incidents investigated, triaged and understood with extra accuracy.
Response: Act rapidly and confidently
As soon as a menace is recognized, the plain subsequent step could be to answer it. As talked about earlier, SOARs do a great job with automating the response section with recognized threats.
The effectivity of this automation, nonetheless, depends closely on information that’s supplied by different sources, i.e. when earlier phases of the SOC workflow can ship usable and dependable outputs that may be despatched to a response software program.
Integrating extra correct information that has been normalized and investigated by expertly engineered automation makes response instruments way more dependable and efficient.
Clearly, not all responses will be automated as attackers proceed to evolve their strategies. In lots of situations, it is necessary for analysts to research incidents completely and enact responses manually. However like the opposite phases of the workflow, the extra that these duties will be automated, the extra safety groups shall be freed as much as deal with extra advanced assaults.
So, why aren’t extra firms utilizing automation?
Many groups know that automation will enhance their productiveness, however altering processes and software program is commonly tough for a number of causes:
- Changing legacy software program is time consuming, costly and doubtlessly dangerous
- Getting stakeholder approval for main implementations is difficult and gradual
- Educating analysts on utilizing new software program takes time and sources
- Ever-evolving assault strategies maintain safety groups occupied with the “right here and now”
These blockers piled on prime of maximum personnel shortages could make the duty appear daunting.
However, as automation continues to take middle stage, the trade will proceed to see important reductions in whole price of possession (TCO), imply time to detection/response (MTTD/MTTR), analyst burnout and CISO frustration.
SOC Platforms to the rescue
When a number of items of the SOC workflow are mixed and automatic, the load and strain of the traditional workload start to dissolve. Analysts will begin to have the ability to wave goodbye to spending lengthy hours bouncing from instrument to instrument, chasing false positives or just sustaining conventional SIEM options.
The brand new technology of SOC platforms have quite a bit to supply, at each stage of the SOC workflow. Having been born within the cloud, SOC platforms are capable of make the most of trendy information architectures to extra simply develop further options and enhancements. This, together with the benefit of with the ability to ingest all safety information at a fraction of the price of legacy instruments, has resulted in a development in the direction of elevated automation embedded in them.
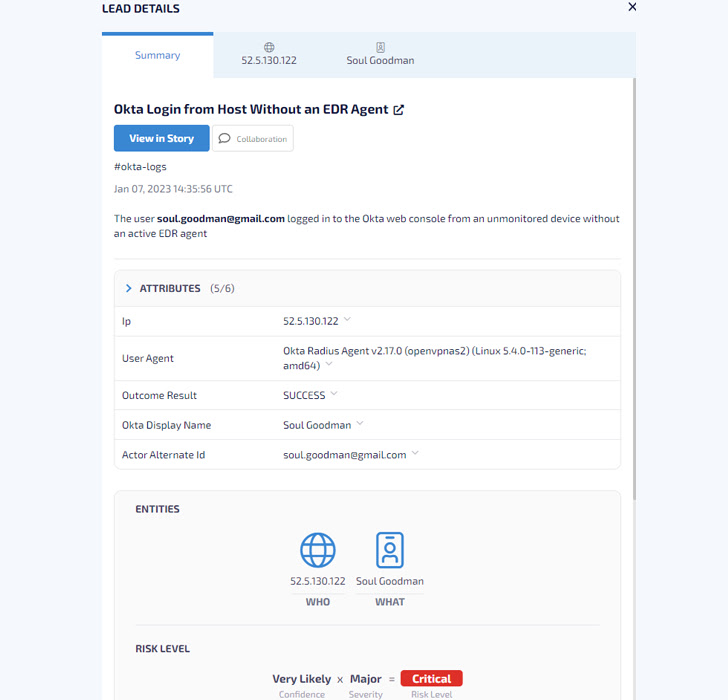 |
| A pattern Auto-Investigation abstract on the Hunters SOC Platform displaying the important thing entities of an alert generated after a consumer logged in to the Okta net console from an unsupervised gadget with out an energetic EDR agent, in addition to the Threat Rating related to it |
An instance of that may be the investigation of threats: that is recognized by most analysts to be a tedious, guide activity, involving sorting by means of countless false positives. However right now’s SOC platforms have launched automation, considerably enhancing the investigation course of. Enhancements like automated cross-source correlation, ML fashions, and built-in information interrogation queries have emerged to assist analysts by means of the repetitive and most laborious menace investigation duties.
Now could be the time to begin leveraging automation because it continues to alter the trade. Groups not actively adopting these improvements will discover themselves behind the curve, doubtlessly leaving their organizations weak and their personnel overwhelmed.
Be taught extra about how Hunters SOC Platform may help your SOC: www.hunters.ai