As many as 350,000 open supply tasks are believed to be doubtlessly weak to exploitation because of a safety flaw in a Python module that has remained unpatched for 15 years.
The open supply repositories span numerous business verticals, reminiscent of software program improvement, synthetic intelligence/machine studying, net improvement, media, safety, IT administration.
The shortcoming, tracked as CVE-2007-4559 (CVSS rating: 6.8), is rooted within the tarfile module, profitable exploitation of which may result in code execution from an arbitrary file write.
“The vulnerability is a path traversal assault within the extract and extractall features within the tarfile module that enable an attacker to overwrite arbitrary information by including the ‘..’ sequence to filenames in a TAR archive,” Trellix safety researcher Kasimir Schulz stated in a writeup.
Initially disclosed in August 2007, the bug has to do with how a specifically crafted tar archive might be leveraged to overwrite arbitrary information on a goal machine merely upon opening the file.
Put merely, a risk actor can exploit the weak spot by importing a malicious tarfile in a fashion that makes it potential to flee the listing {that a} file is meant to be extracted to and obtain code execution, permitting the adversary to doubtlessly seize management of a goal machine.
“By no means extract archives from untrusted sources with out prior inspection,” the Python documentation for tarfile reads. “It’s potential that information are created exterior of path, e.g. members which have absolute filenames beginning with “https://thehackernews.com/” or filenames with two dots ‘..’.”
The vulnerability can also be paying homage to a just lately disclosed vulnerability in RARlab’s UnRAR utility (CVE-2022-30333) that would result in distant code execution.
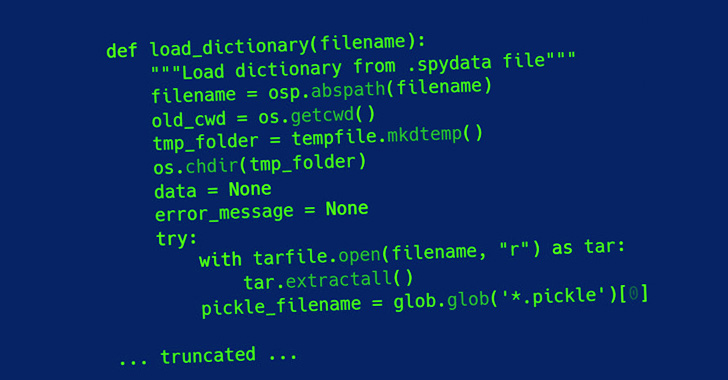
Trellix has additional launched a customized utility known as Creosote to scan for tasks weak to CVE-2007-4559, utilizing it to uncover the vulnerability within the Spyder Python IDE in addition to Polemarch.
“Left unchecked, this vulnerability has been unintentionally added to lots of of hundreds of open- and closed-source tasks worldwide, creating a considerable software program provide chain assault floor,” Douglas McKee famous.